TB - GNS3 Lab: VACL (VLAN Access Lists) with GNS3Vault
by C. Casquatch
In this blog, I walk through the lab step-by-step and include screenshots to document my process and learning.
Using Rene Molenaar’s GNS3 Vault lab
🔒 Blocking Ping in the Same VLAN Using VACLs on a Cisco Switch
Have you ever needed to block ping (ICMP) traffic between two devices on the same VLAN, while still allowing other types of communication? Traditional router-based ACLs won’t help in this case, because Layer 2 switches forward traffic within the same VLAN without routing it.
That’s where VACLs (VLAN Access Control Lists) come in.
🧱 What Are VACLs?
VACLs apply access control policies within a VLAN, regardless of whether traffic is being bridged (switched) or routed. Unlike port-based ACLs (PACLs), which only apply to ingress traffic on a switchport, VACLs apply to all traffic within the specified VLAN(s).
This is especially useful for enforcing security policies between same-subnet hosts on a switch.
🧾 Lab Scenario
You have a topology like this:
- SW1 (Layer 2 switch)
- DNS1 connected to
gi0/0, IP:192.168.10.1 - DNS2 connected to
gi0/1, IP:192.168.10.2 - Both hosts are in VLAN 10
🎯 Goal: Prevent DNS1 and DNS2 from pinging each other (block ICMP), but allow all other traffic.
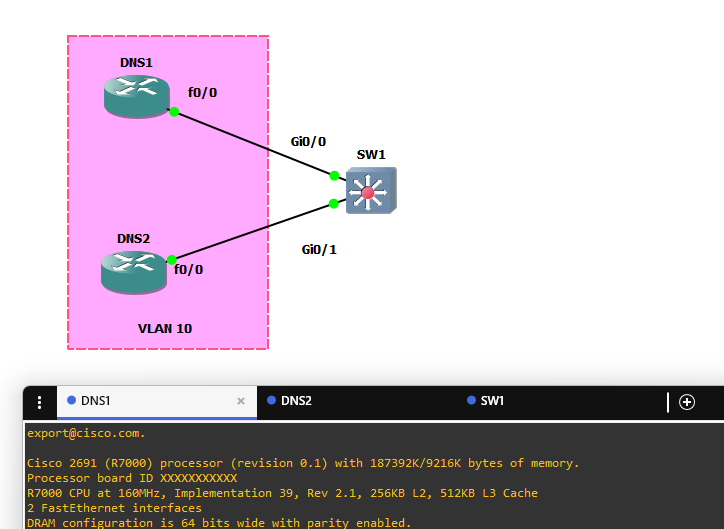
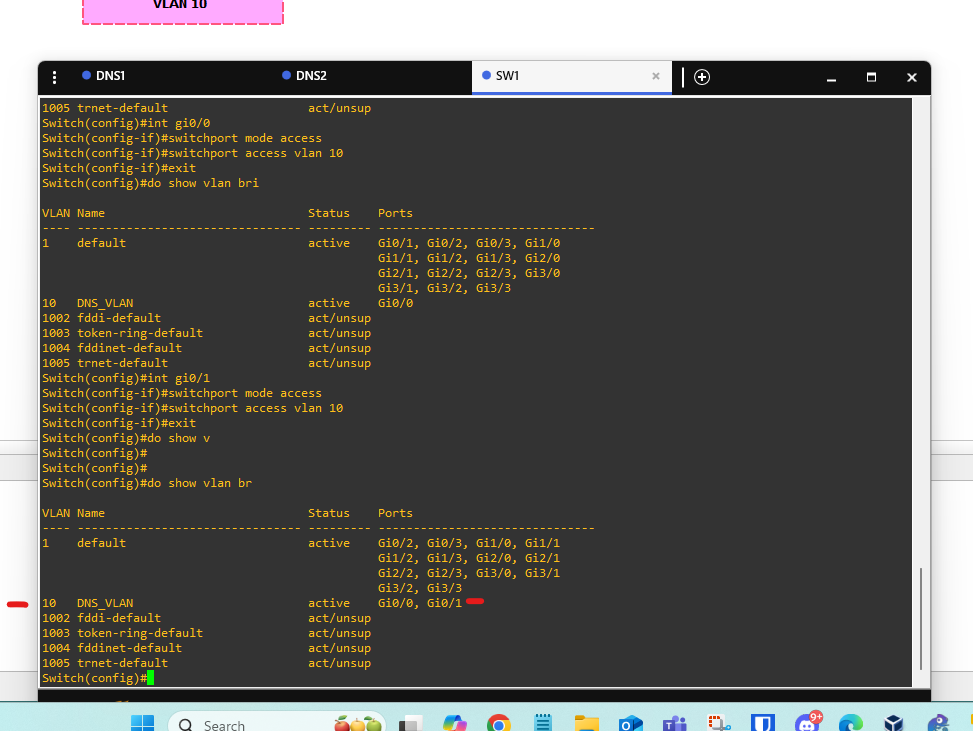
🔧 Step 1: Assign Ports to VLAN 10
Configure both switchports as access ports in VLAN 10.
conf t
interface gi0/0
switchport mode access
switchport access vlan 10
!
interface gi0/1
switchport mode access
switchport access vlan 10
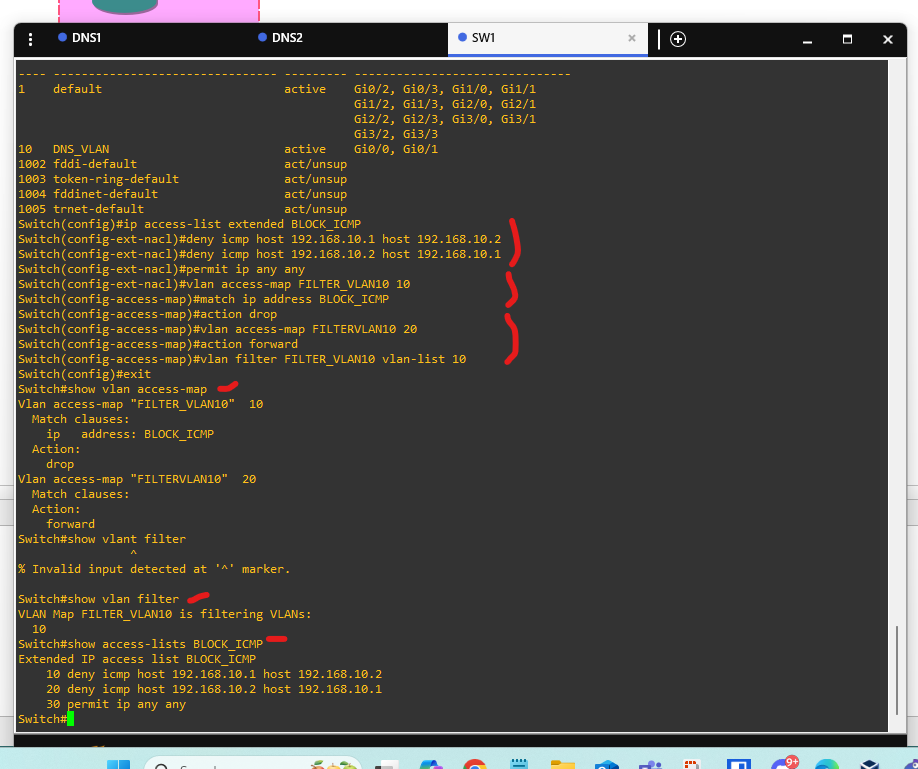
🔧 Step 2: Create an Extended ACL
We’ll use an extended ACL to match ICMP traffic between the two hosts.
ip access-list extended BLOCK_ICMP
deny icmp host 192.168.10.1 host 192.168.10.2
deny icmp host 192.168.10.2 host 192.168.10.1
permit ip any any
🔧 Step 3: Create a VLAN Access Map
Bind the ACL to an action using a VLAN access map.
vlan access-map FILTER_VLAN10 10
match ip address BLOCK_ICMP
action drop
!
vlan access-map FILTER_VLAN10 20
action forward
🔧 Step 4: Apply the Access Map to VLAN 10
vlan filter FILTER_VLAN10 vlan-list 10
🔍 Verification Commands
Check your configuration using the following commands:
show vlan access-map
show vlan filter
show access-lists BLOCK_ICMP
🧪 Testing
- From DNS1:
ping 192.168.10.2➡️ Should fail
- Test other traffic (e.g.,
telnet,ssh) to confirm it still works. (I did not have the patience to configure telnet to make sure it worked so I stopped at making sure that the pings failed in this lab.)
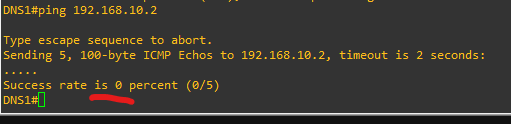
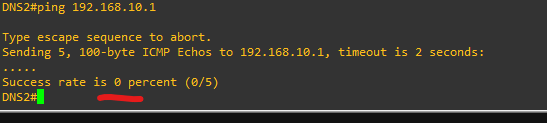
✅ Result
- DNS1 and DNS2 cannot ping each other.
- All other communication is allowed.
- Filtering is enforced at Layer 2 using VLAN ACLs.
Happy switching! 🧠🔧
tags: GNS3 - vlans - Networking - access lists