TryHackMe's SOC Analyst Level 1 Path
by C. Casquatch
This project consists of practicing the following: Monitoring and investigating alerts,configuring and managing security tools, developing and implementing IDS signatures. This learning path is created by the team at TryHackMe - at the end of the journey, the reward is satisfaction and a cert to show your friends.

~ I have edited out the certificate number that should be present in the top right corner.
Languages and Utilities Used
PowerShell, Linux, nmap, Mitre and Att&ck, Yara, OpenCTI, MISP, Snort, NetworkMiner, Zeek, Brim, Wireshark, Cisco Talos, Sysinternals, Sysmon, Osquery, Wazuh, ELK, Splunk, Autopsy, Redline, KAPE, Volatility, Velociraptor, Phishtool, Hybrid Analysis, Virus Total
Environments Used
- Windows 10
- Kali Linux
- Ubuntu
Program walk-through:
This is a broad overview of this learning path:
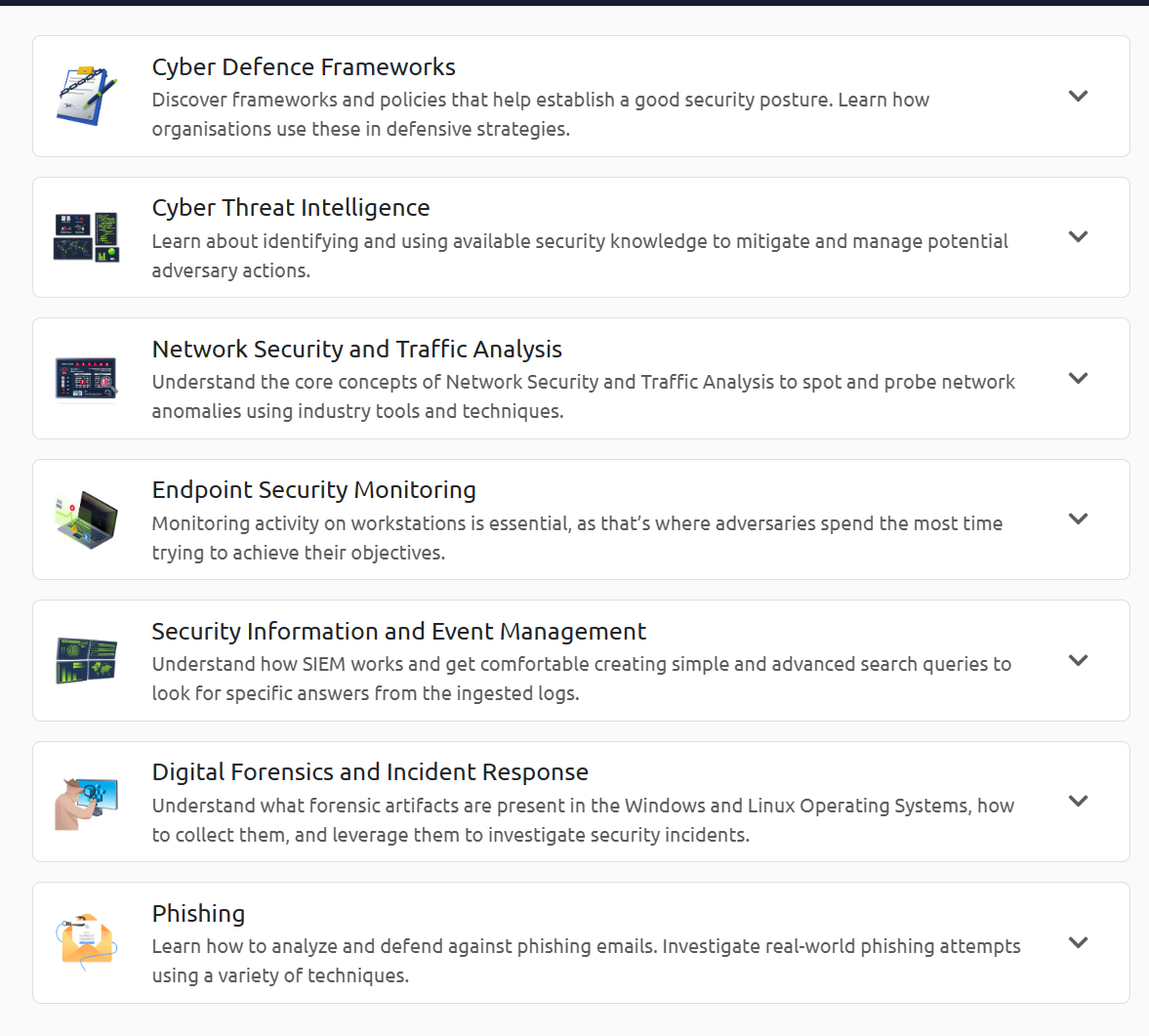
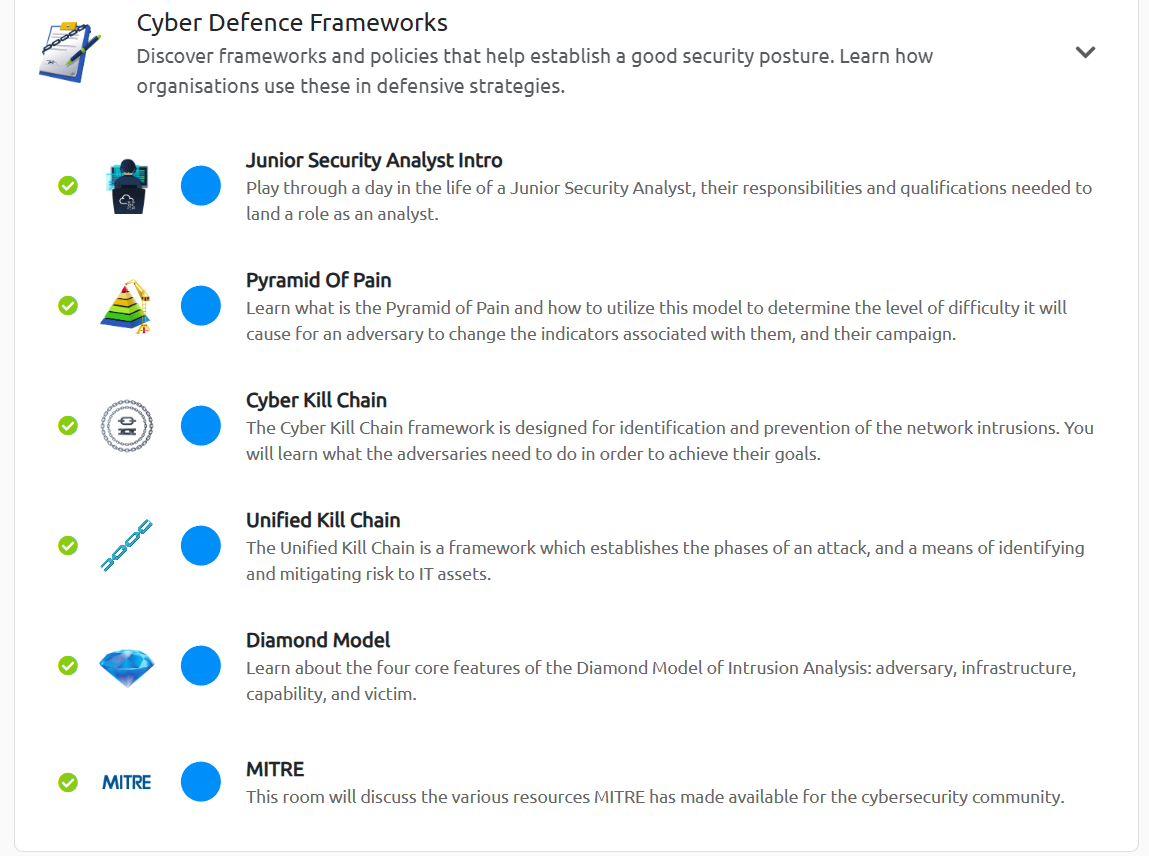
- Cyber Defence Frameworks, learning what is involved with being a SOC Analyst and the basic principles behind the role.
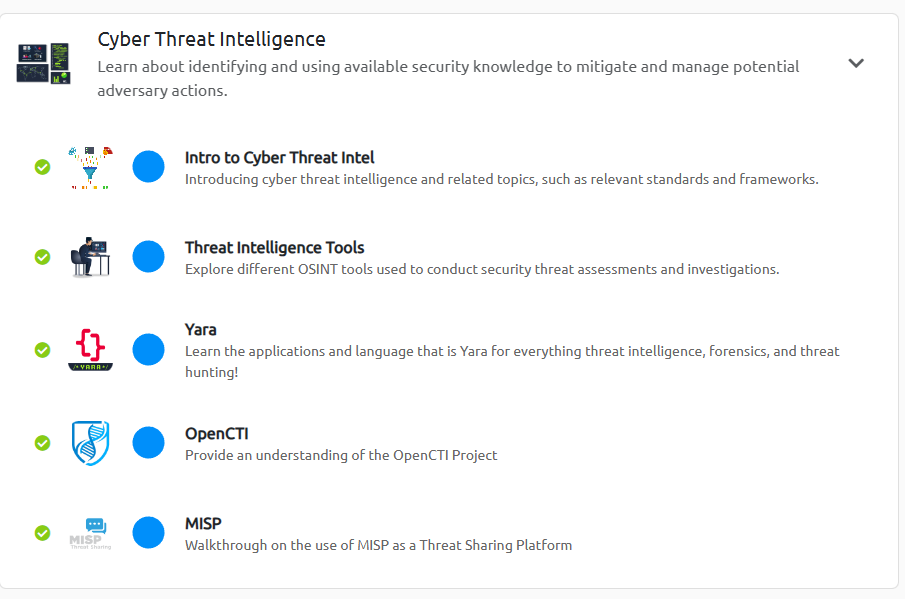
- Cyber Threat Intelligence, this series of rooms introduced CTI and various frameworks used to share intelligence.
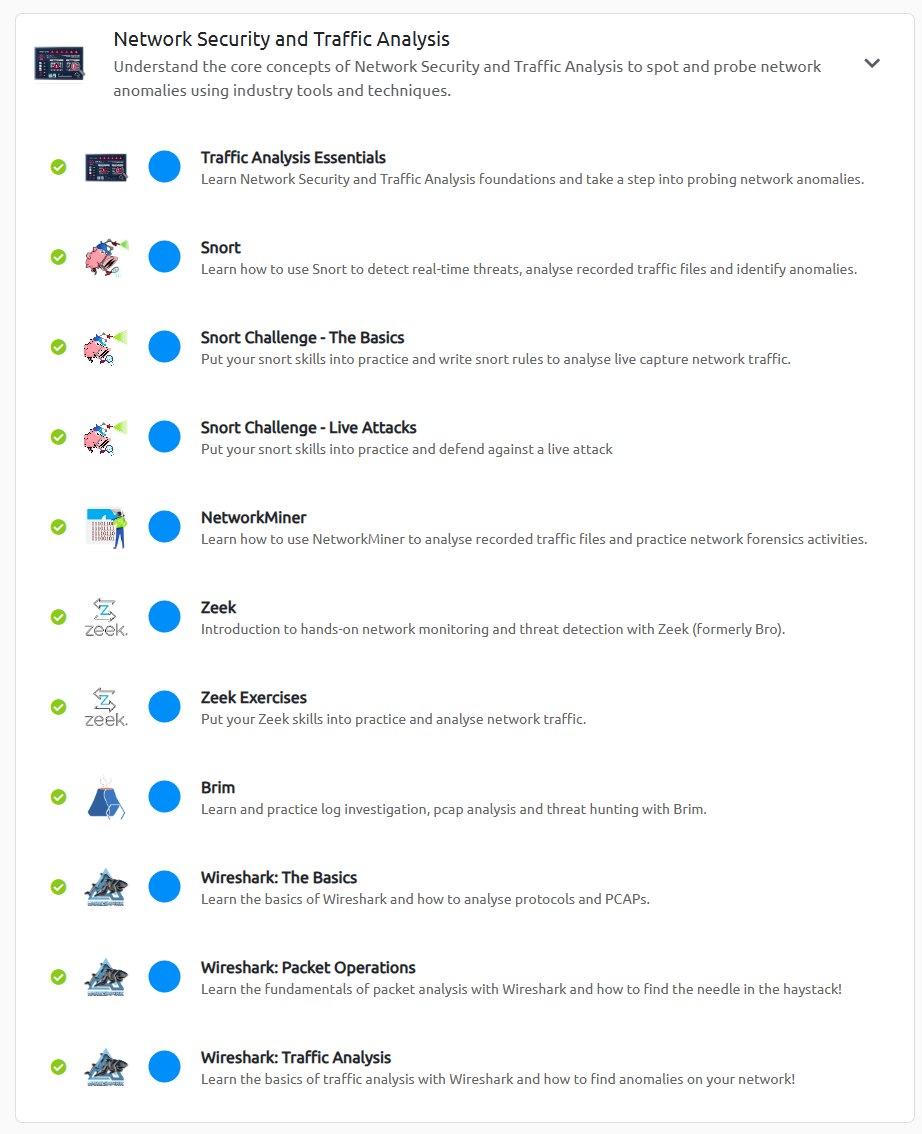
- Network Security and Traffic Analysis, introduced the essential concepts of network security and traffic analysis to assist with traffic/packet analysis.
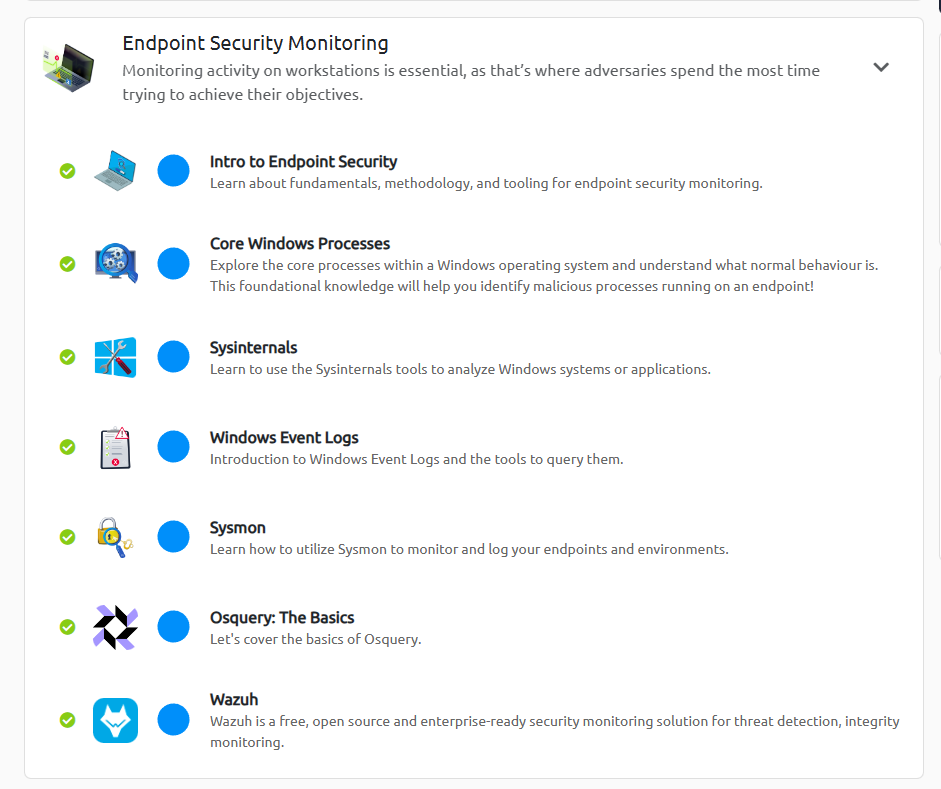
- Endpoint Security Monitoring, tackled the following; endpoint security fundamentals, endpoint logging and monitoring, and endpoint log analysis.
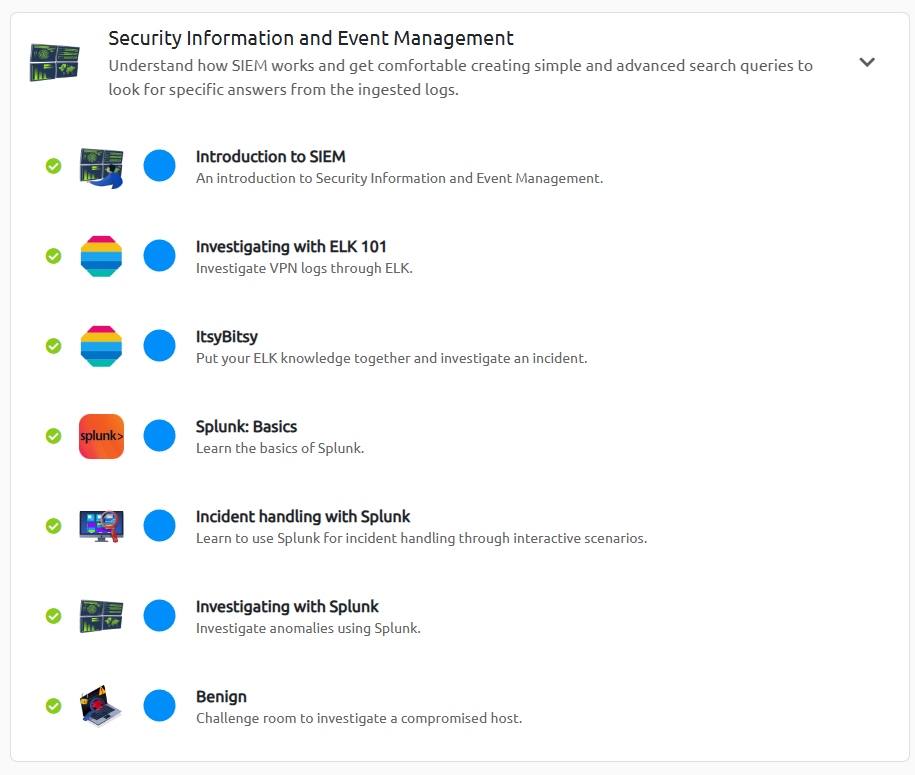
- Security Information and Event Management, how SIEM’s work and the capabilities it provides for network visibility, log sources, and log ingestion.
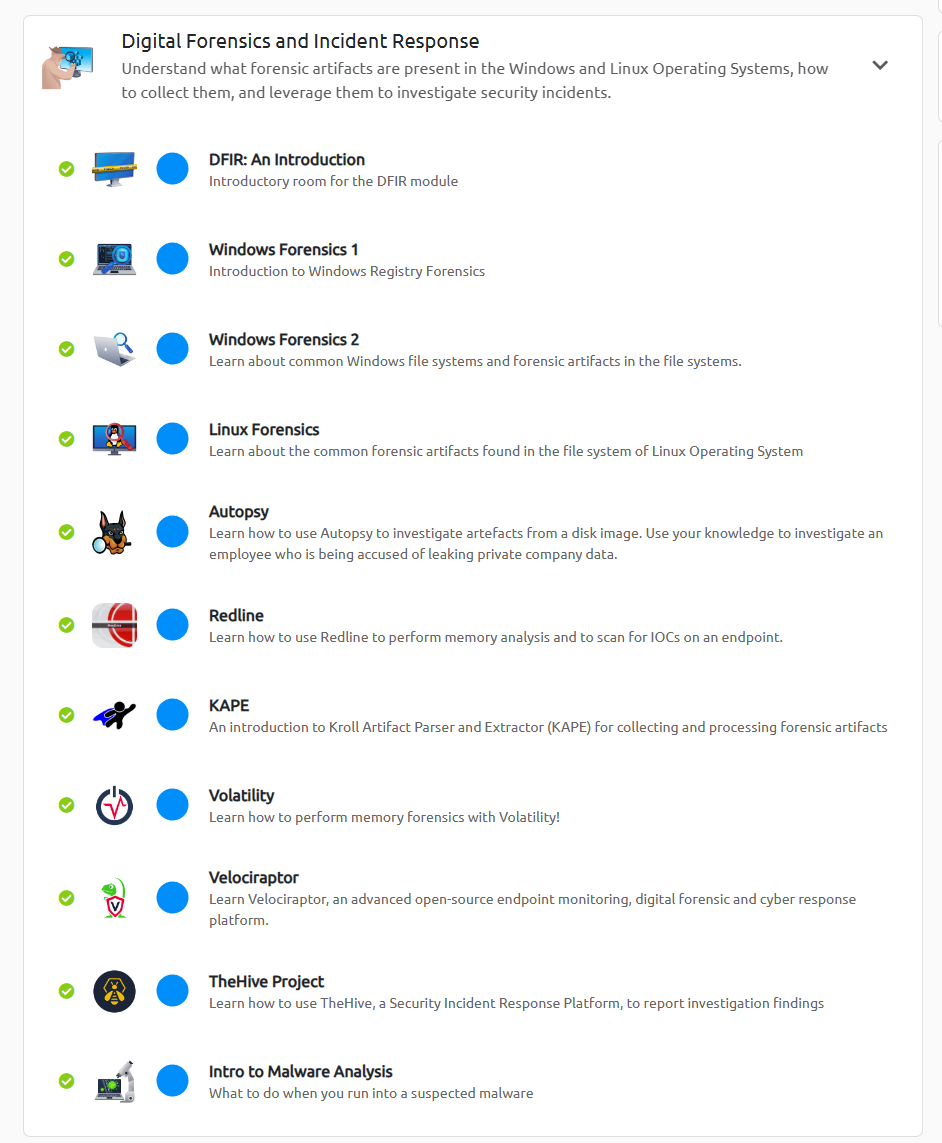
- Digital Forensics and Incident Response, basic DFIR concepts and the tools available for use in the incident response process.
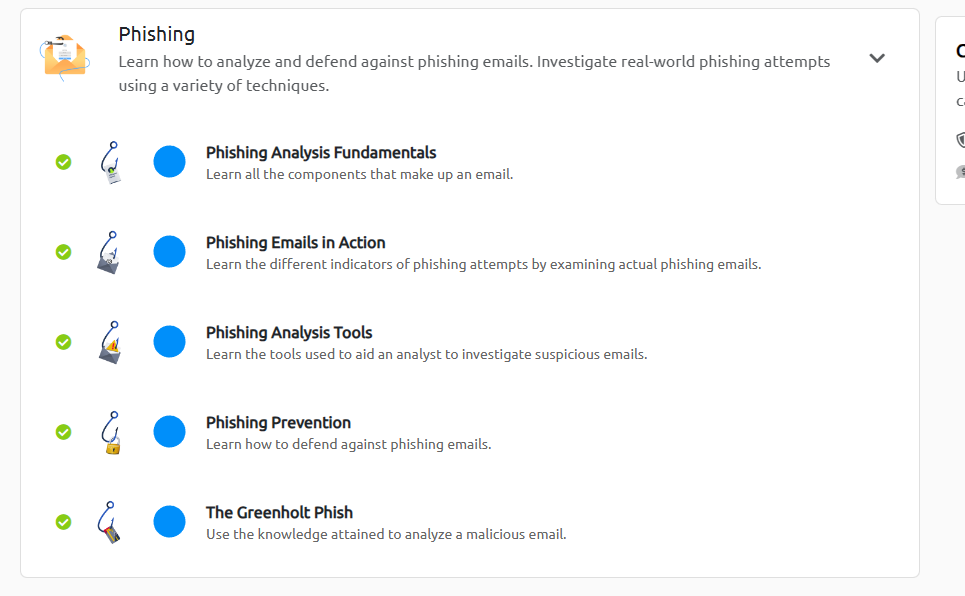
- Phishing, looking at the components involved with sending emails across the internet and how to analyse email headers.
Each of the seven sections has a series of rooms to complete, these rooms allowed for theoretical and practical examinations of the topic
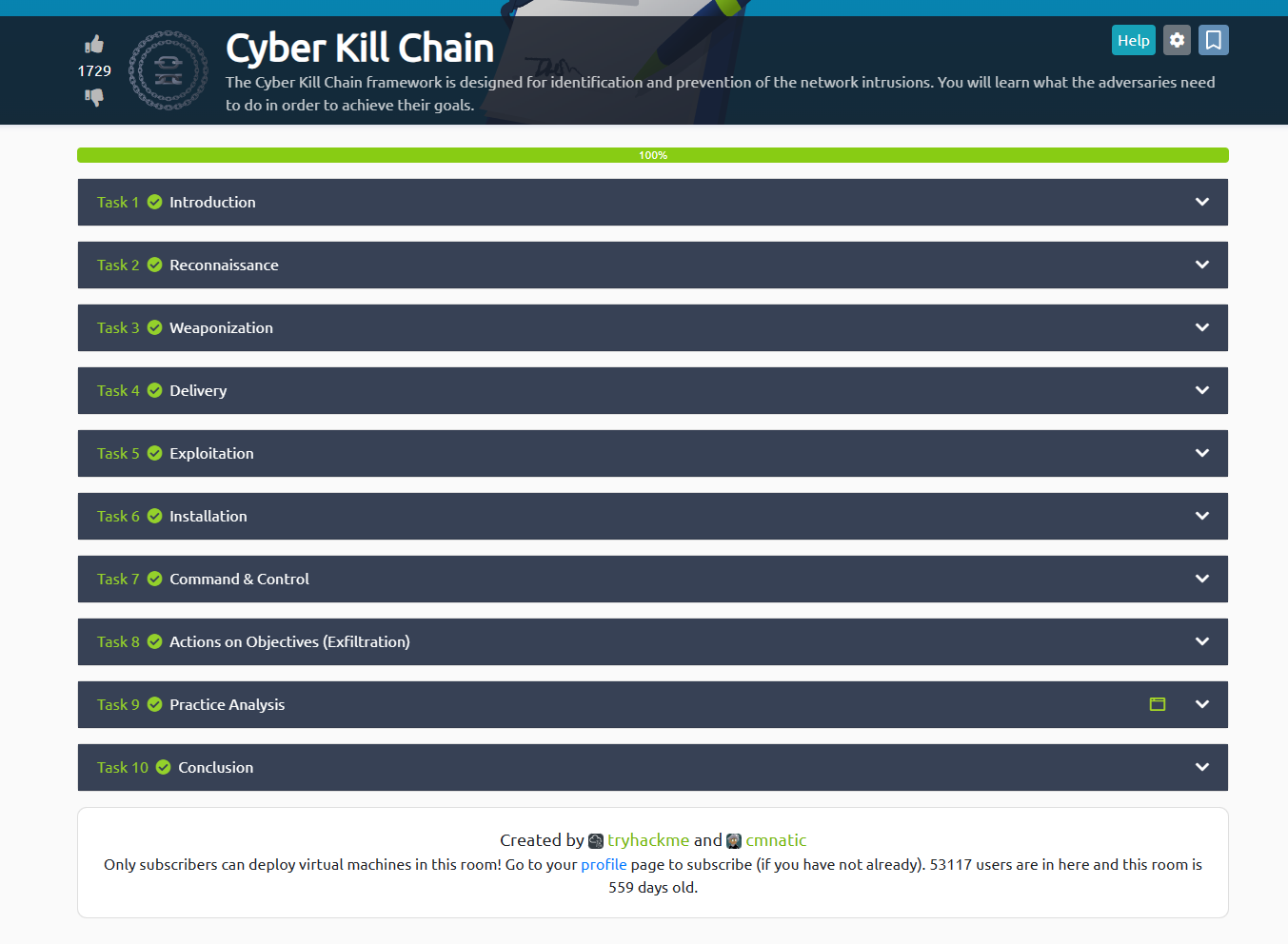
Each room has a series of ‘Tasks’ that are required to be completed. Some only require to be read, while others are more in depth and require practice to obtain the answers and move on to the next question
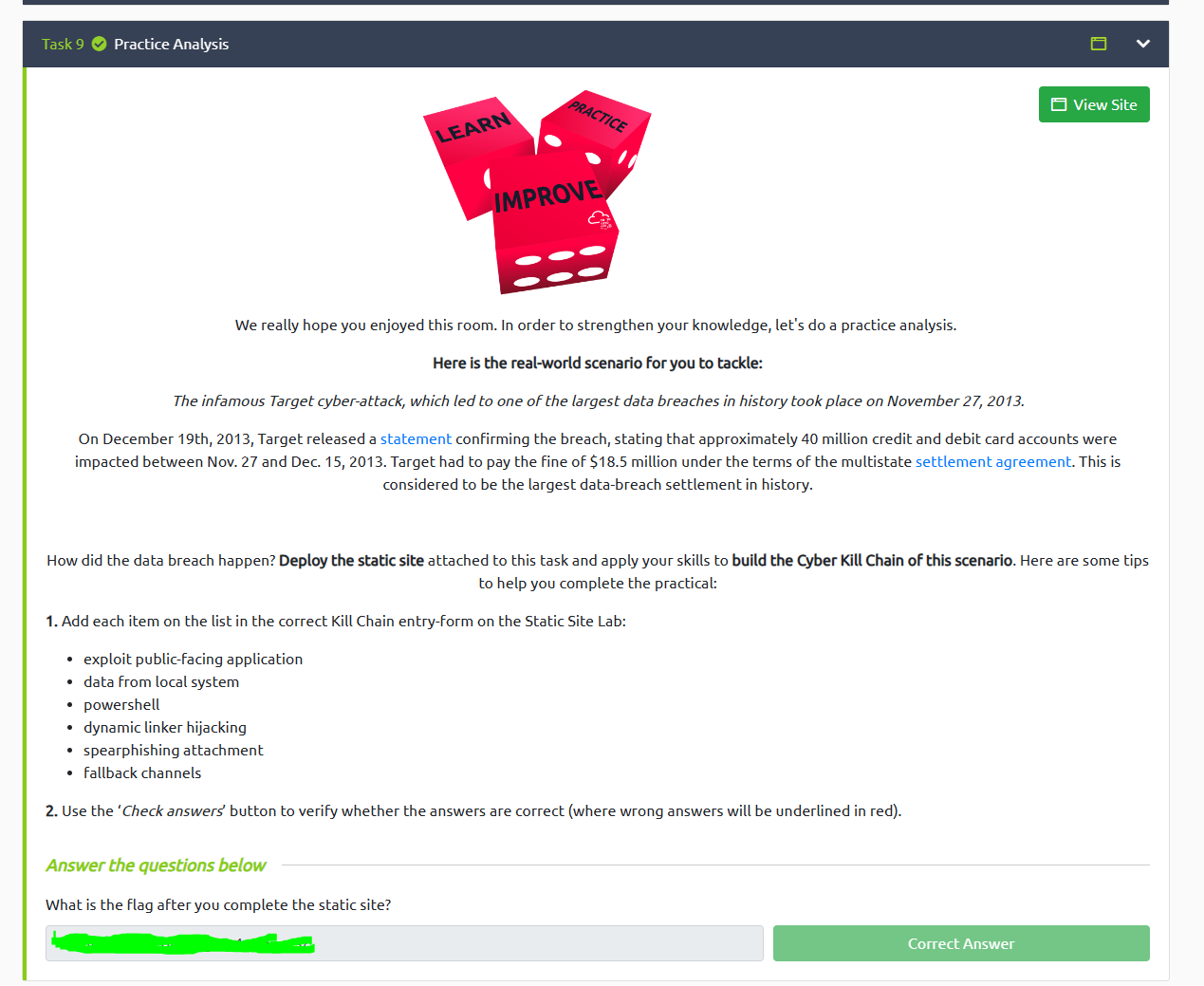
Here is an example of a practical task
Cyber Threat Intelligence Rooms
Network Security and Traffic Analysis Rooms
Endpoint Security Monitoring Rooms
SIEM (Security Information and Event Management) Rooms
Digital Forensic and Response Rooms
Phishing Rooms
tags: SOC - tryhackme