TB Reaper
by C. Casquatch
scenario: Our SIEM alerted us to a suspicious logon event which needs to be looked at immediately. The alert details were that IP Address and the Source Workstation name were a mismatch. You are provided a network capture and event logs from the surrounding time around the incident time. Corelate the given evidence and report back to your SOC Manager.
Key words: “IP Address and the Source Workstation name were a mismatch”
Let’s start by opening the PCAP file in Wireshark. Going over Statistics-> Endpoints we can see top most IP Addresses.
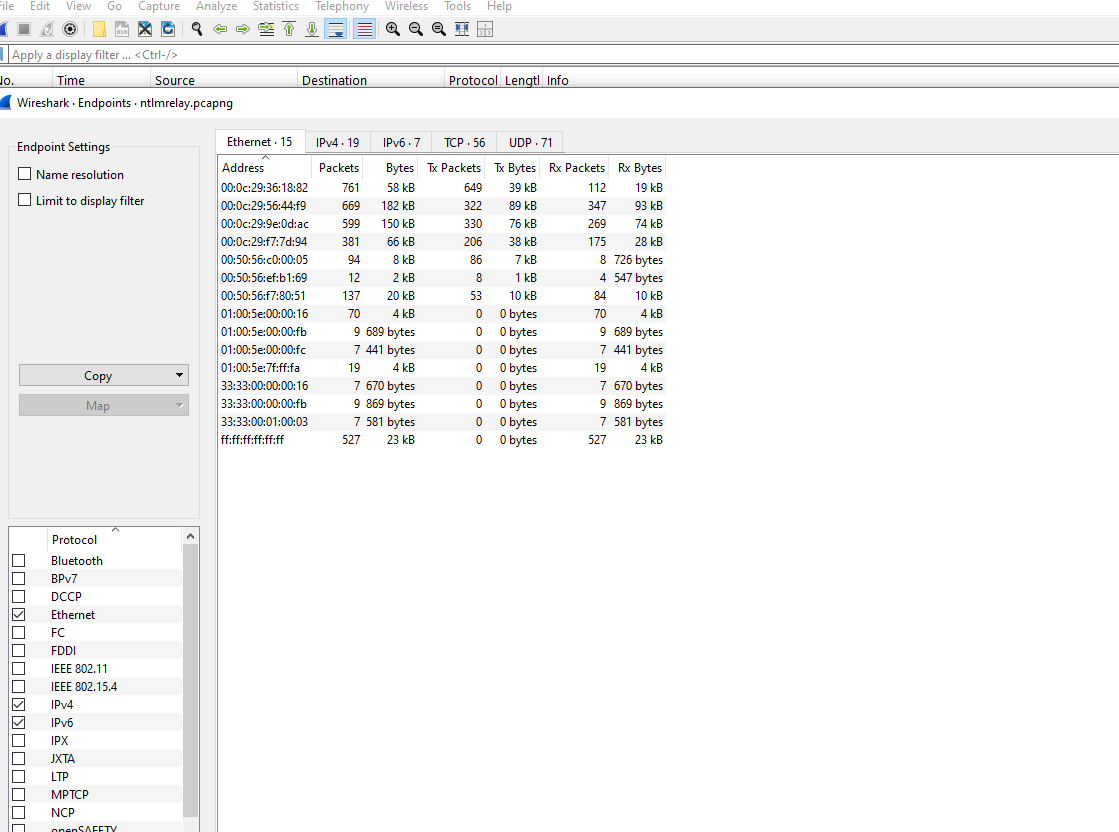
Q1: what is the IP address for Forela-Wkstn001?
Hint : Filter for nbns protocol to find the relevant IP Address. More info about NBNS here: https://wiki.wireshark.org/NetBIOS/NBNS
Let’s get filtering.
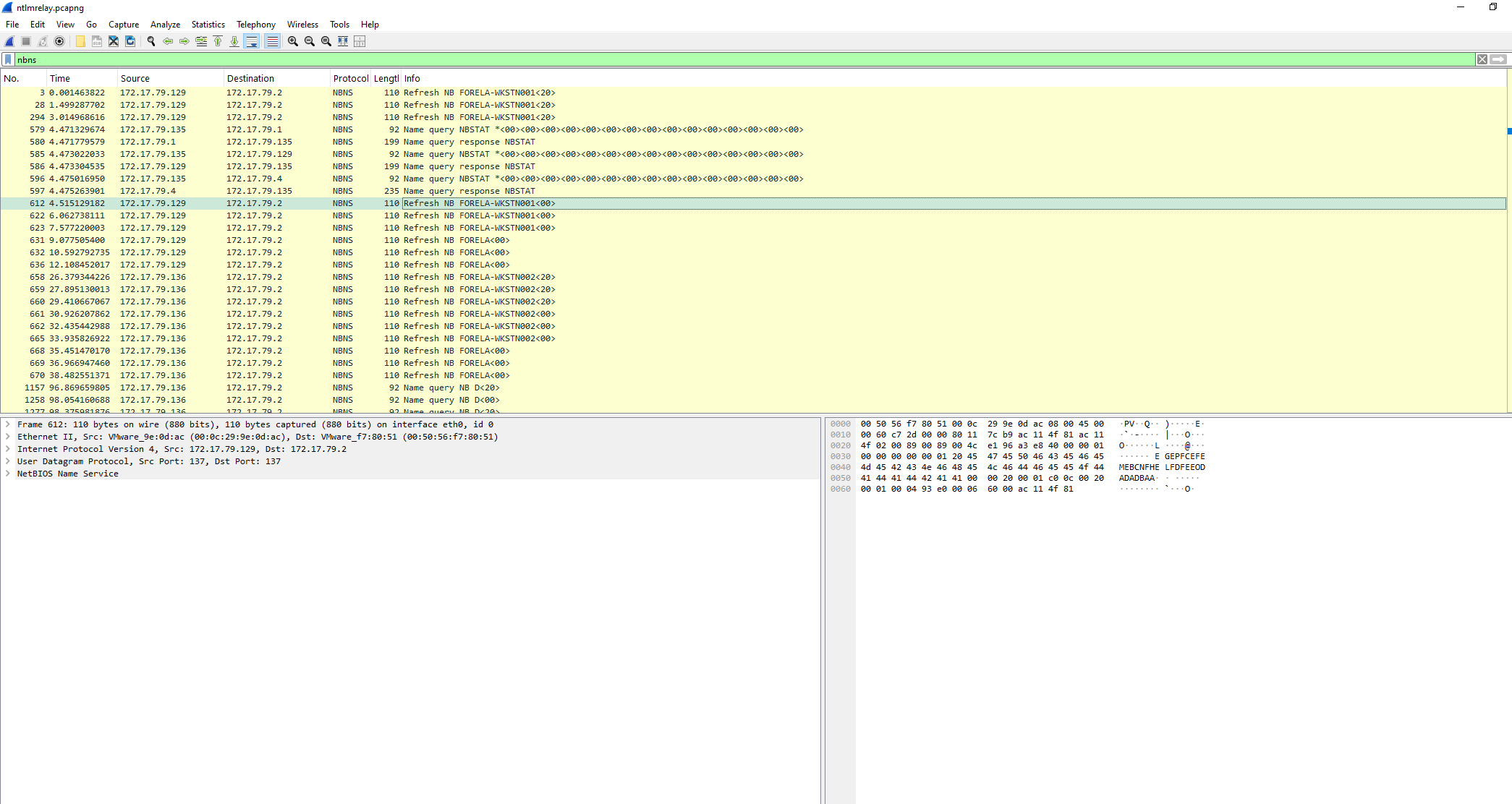
We look at the SOURCE IP.
Question 2: What is the IP Address for Forela-Wkstn002?
Look below Forela-Wkstn001 for Forela-Wkstn002 and in the SOURCE IP we have our answer.
Q3: What is the username of the account whose hash was stolen by attacker?
Hint: Filter for ntlmssp protocol in wireshark OR Filter for 4624 event ID and Look for an odd looking logon event. More about NTLMSSP: https://en.wikipedia.org/wiki/NTLMSSP
Let’s start with wireshark -
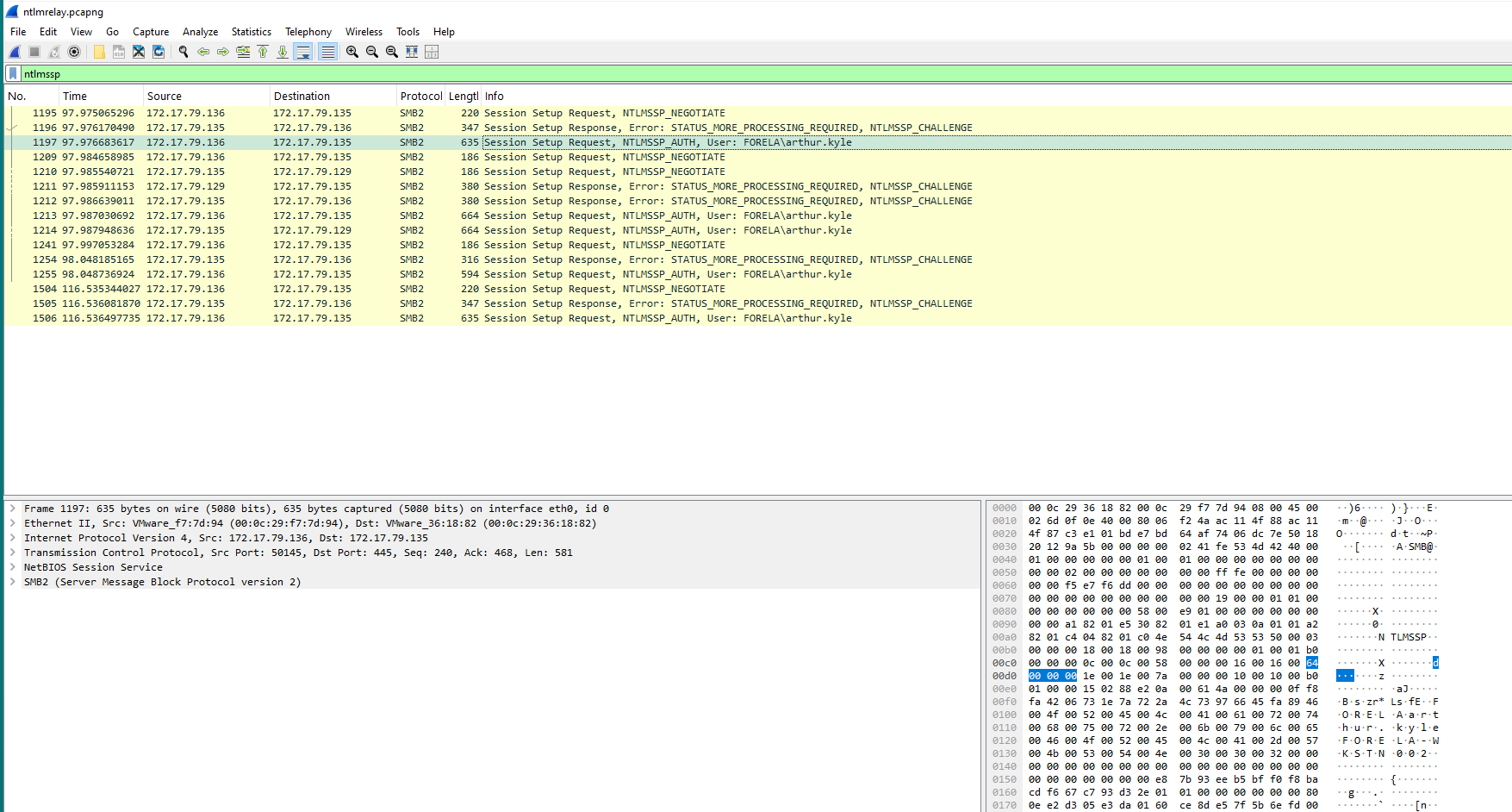
I’m going to assume for a hot second that it is the only other username here.
Q4: What is the IP Address of Unknown Device used by the attacker to intercept credentials?
Hint: Look for an IP Address that do not belong to any workstation but is involved in authentication flow for the victim user. Alternatively you can also filter for NBNS protocol and the device with no hostname is the device we looking for. Another method is to look for the anomalous logon event and see the source IP Address.
In the previous screenshot, there is an IP address “172.17.79.135” without a workstation but is involved with the flow of the victim user. The protocol here is smb2 which we can look at along with the IP address to see if we find anything else.
to filter we can use: smb2 and ip.addr == 172.17.79.135
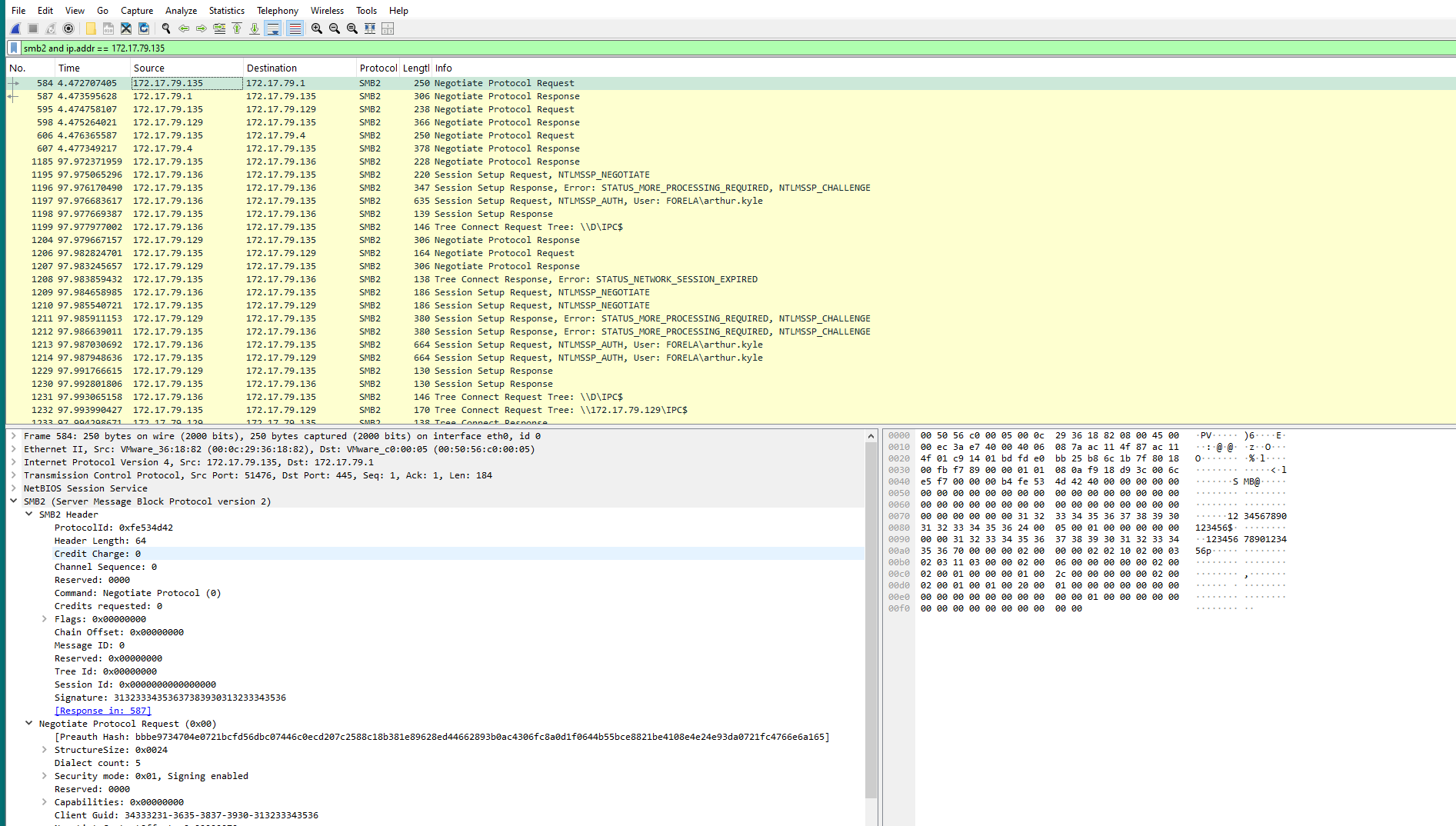
Here it is negotiating with no workstation attached. We will try to put this in as the answer. Hopefully it sticks. And it does.
Q5: What was the fileshare navigated by the victim user account? Hint: Filter for smb2 traffic in wireshark. Search for keywords “BAD_NETWORK_NAME” in packet details. Now look for any file share path which seems like a legit path a day to day user might visit.
Our filter:
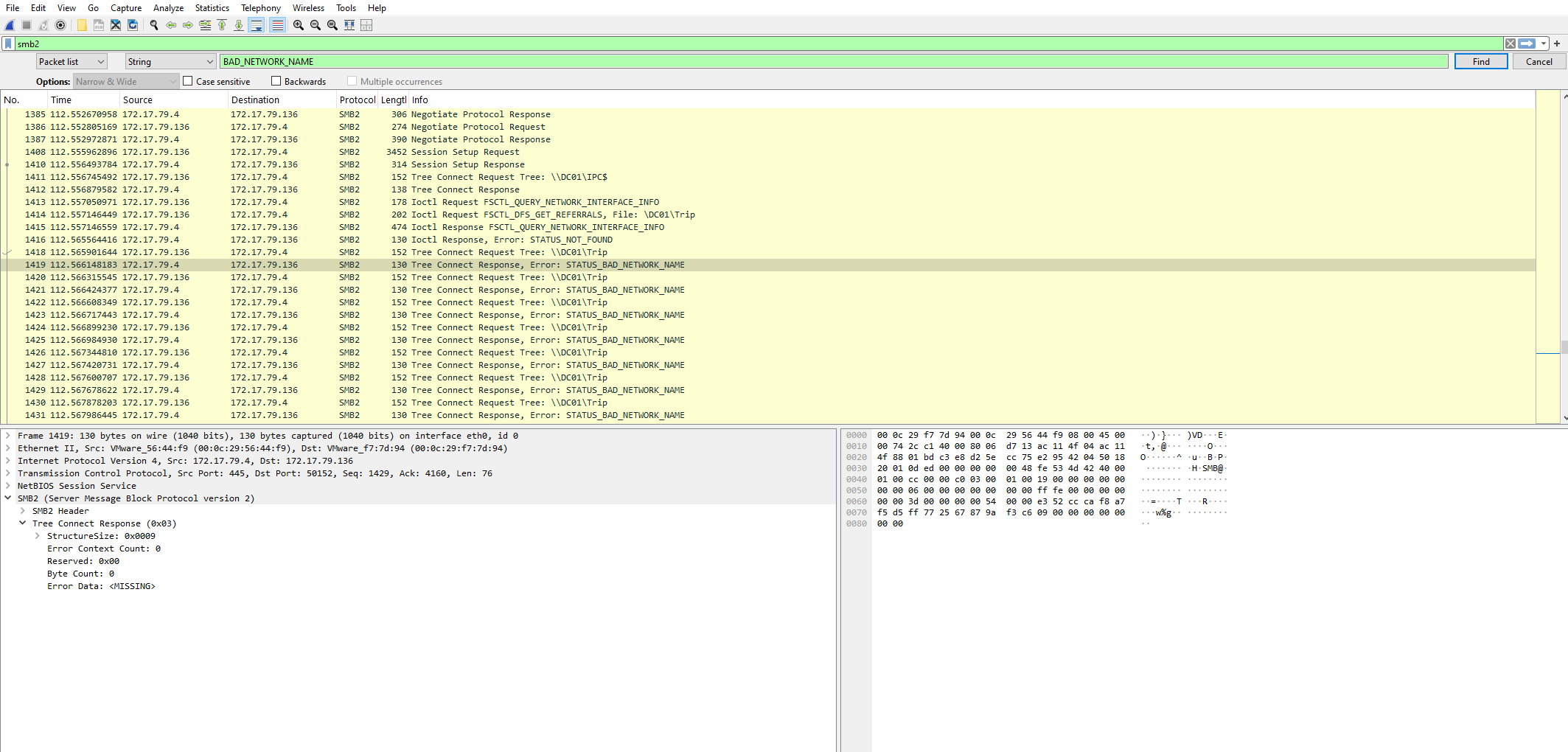
Question 6: What is the source port used to logon to target workstation using the compromised account?
Hint: In provided Event logs, filter for event ID 4624 and look for an event where Security ID is NULL and logon type is 3.The logon process value will be NtlmSSP and authentication package value is NTLM. Then look for Source Port value in event details.
Just filter on the event id 4624 and look through the 11 logs.
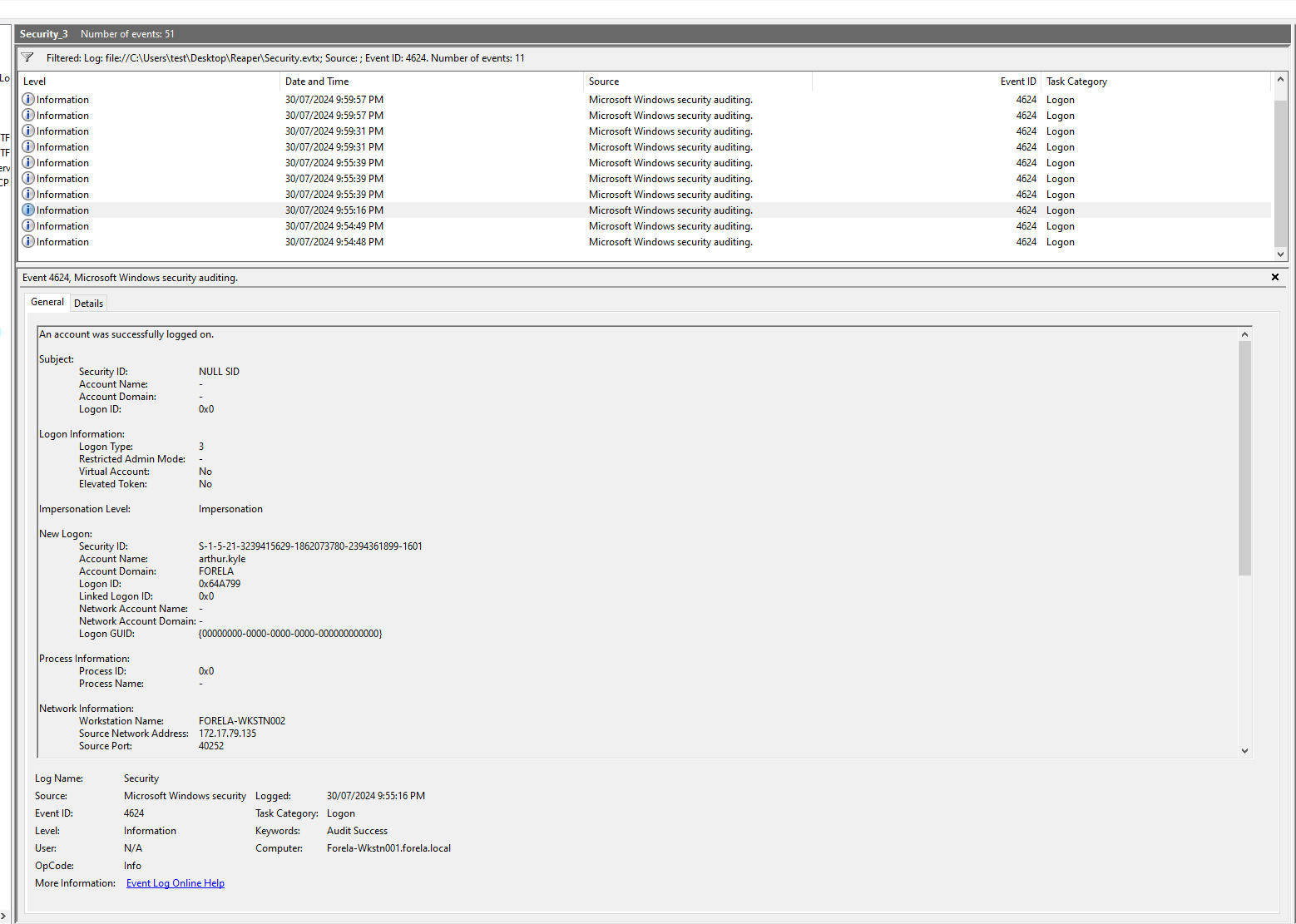
When looking through the logs now we can further narrow down the logon type, which is 3 and the security ID being NULL. I tried making a query in XML and I couldn’t get it to work. Maybe you’ll have more luck:
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">
*[System[(EventID=4624)]]
and
*[EventData[Data[@Name='TargetUserSid'] = 'S-1-0-0']]
and
*[EventData[Data[@Name='LogonType'] = '3']]
</Select>
</Query>
</QueryList>
Q7: What is the Logon ID for the malicious session?
Head to the details tab of the event we just looked at. Take note of the ‘TargetLogonID’
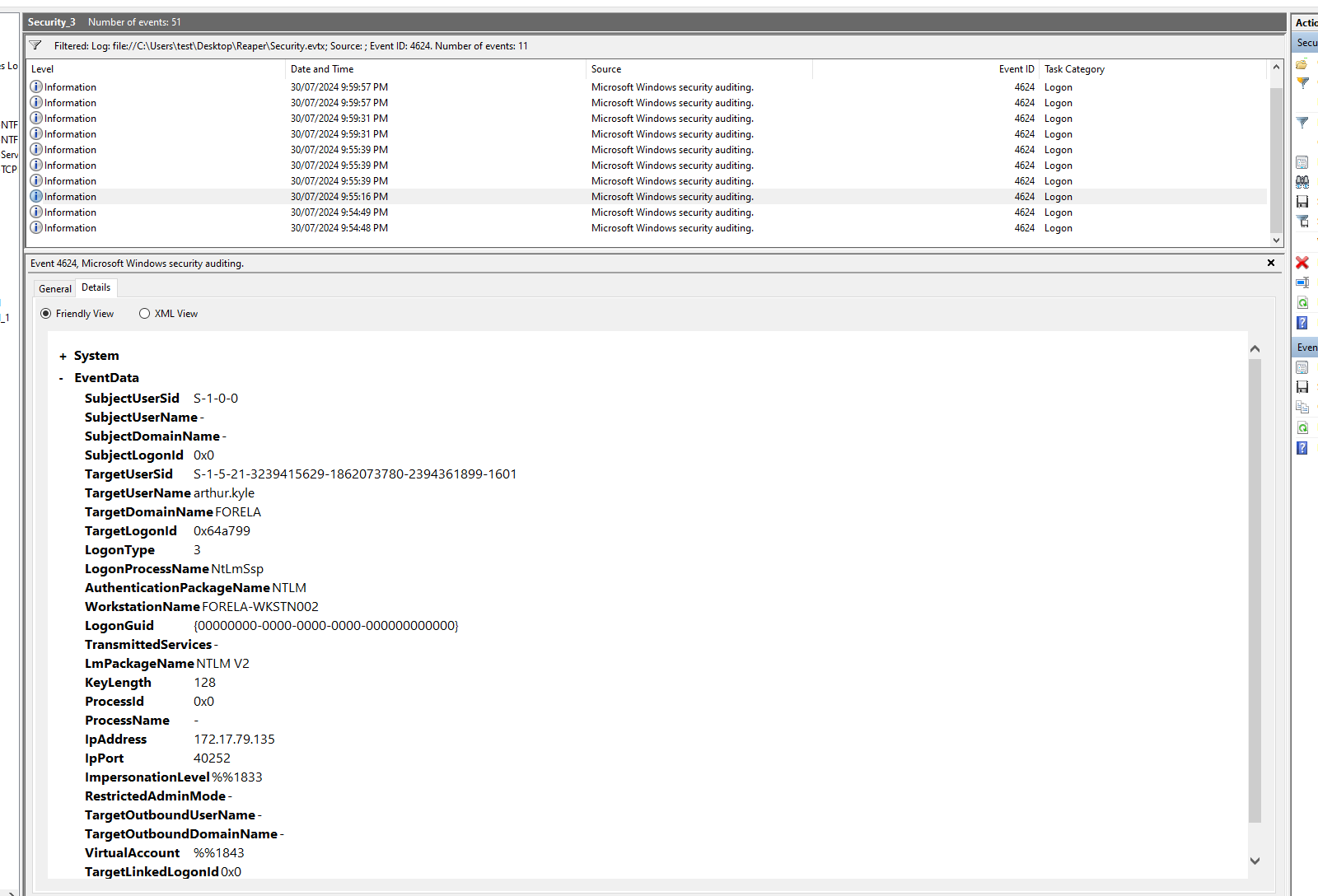
Q8!! The detection was based on the mismatch of hostname and the assigned IP Address.What is the workstation name and the source IP Address from which the malicious logon occur?
In a previous question we identified 172.17.79.135 as an IP that did not belong to any of the workstations. But here we can see it is matched with a workstation name that would usually be assigned to 172.17.79.136..
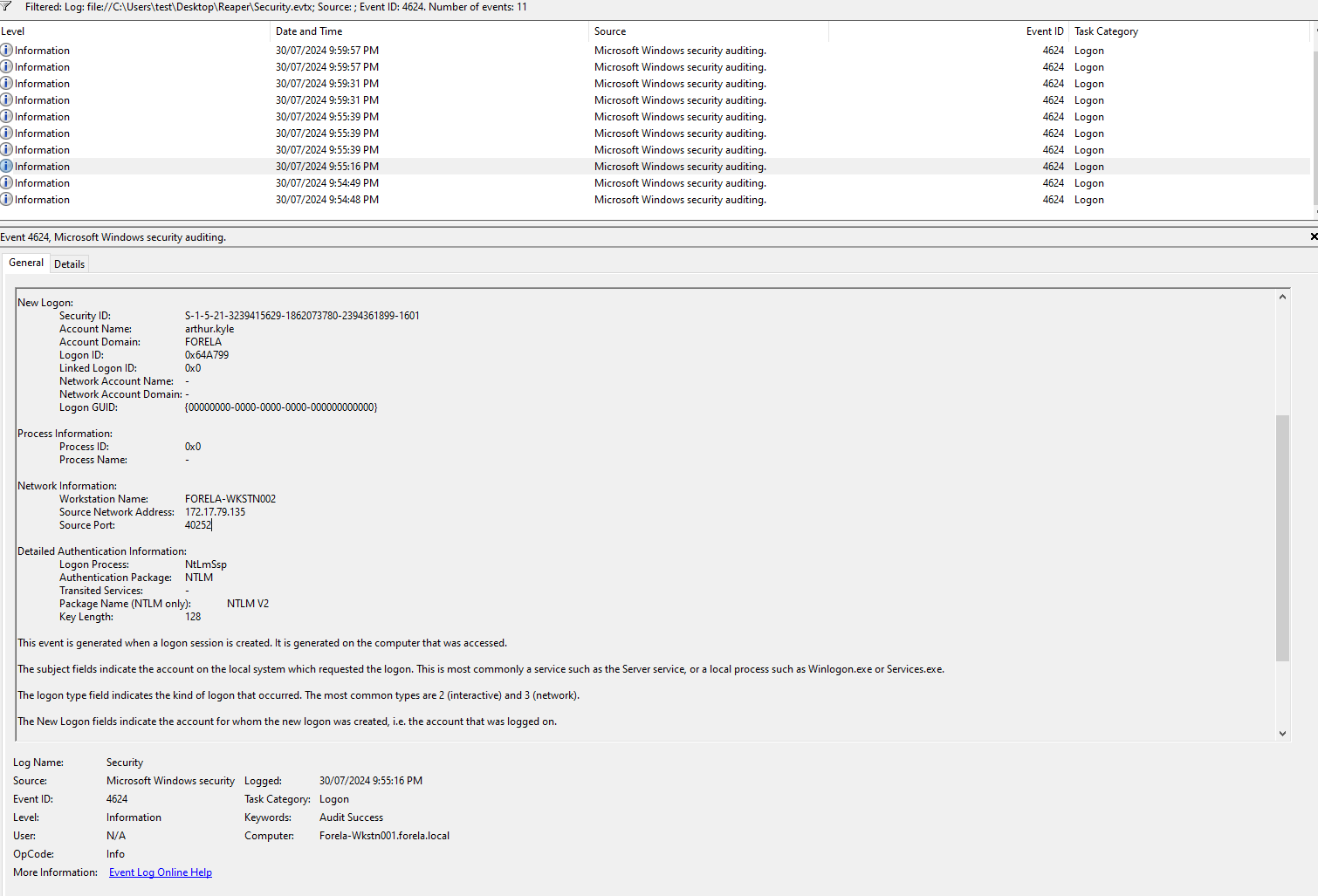
Question noine: At what UTC time did the the malicious logon happen?
Keep looking in the same log event - head to the details tab and open the system section - this is where we can find the UTC time.
Q10: What is the share Name accessed as part of the authentication process by the malicious tool used by the attacker?
Hint: Look for event ID 5140 and see the share name accessed. We can corelate this event with the malicious session via the Logon ID we found before Why we are looking at event id 5140, a network share object was accessed: https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-10/security/threat-protection/auditing/event-5140
The answer they want is under the ‘Share information’ which can be found in the general tab or in the eventdata in the details tab under sharename.
tags: windows - event logs - htb - reaper - wireshark - 4624 - 5140